Microsoft Security Compliance and Identity Fundamentals 온라인 연습
최종 업데이트 시간: 2025년11월16일
당신은 온라인 연습 문제를 통해 Microsoft SC-900 시험지식에 대해 자신이 어떻게 알고 있는지 파악한 후 시험 참가 신청 여부를 결정할 수 있다.
시험을 100% 합격하고 시험 준비 시간을 35% 절약하기를 바라며 SC-900 덤프 (최신 실제 시험 문제)를 사용 선택하여 현재 최신 198개의 시험 문제와 답을 포함하십시오.
정답:
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/get-started-with-service-trust-portal?view=o365-worldwide
정답:
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/get-started-core-ediscovery?view=o365-worldwide

정답: 
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/security/fundamentals/customer-lockbox-overview
정답:
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/dlp-learn-about-dlp?view=o365-worldwide
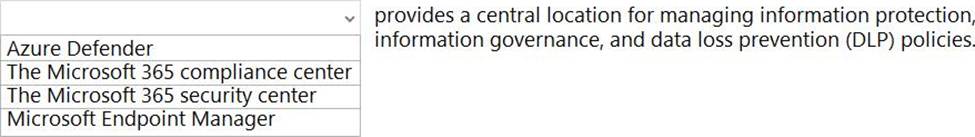
정답: 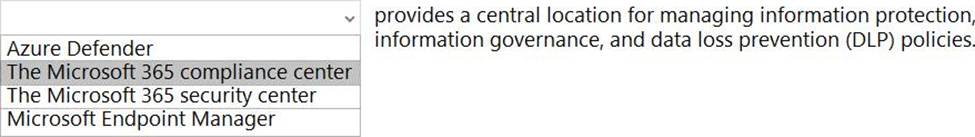
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/compliance/microsoft-365-compliance-center?view=o365-worldwide
MIP capabilities are included with Microsoft 365 Compliance and give you the tools to know your data, protect your data, and prevent data loss.
https://docs.microsoft.com/en-us/microsoft-365/compliance/information-protection?view=o365-worldwide
정답:
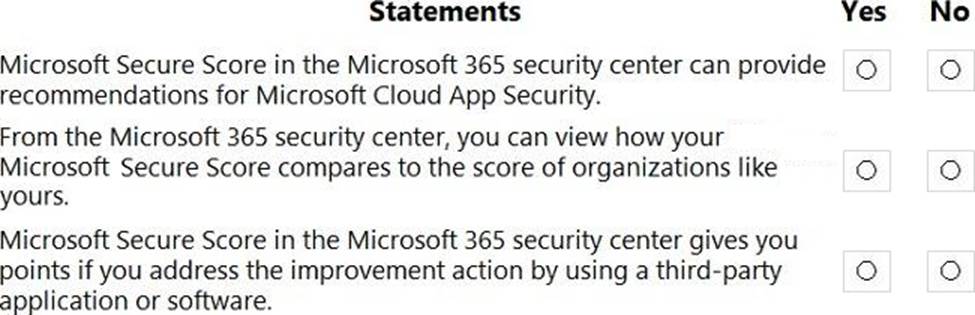
정답: 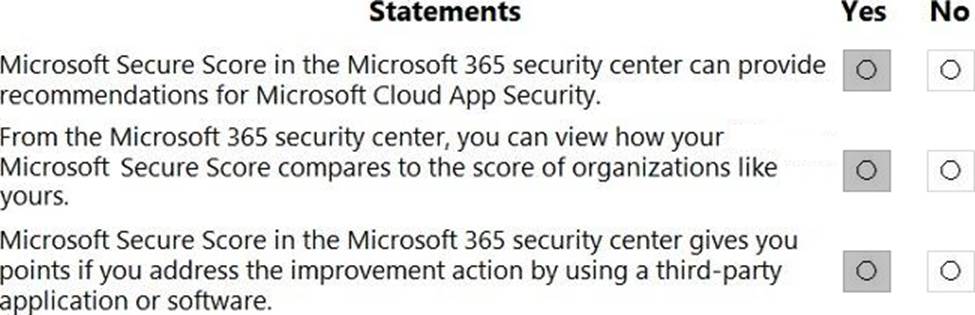
정답:
정답:
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/security/defender/eval-overview?view=o365-worldwide
정답:
Explanation:
Reference: https://docs.microsoft.com/en-us/office365/servicedescriptions/office-365-advanced-threat-protection-service-description

정답: 
정답:
Explanation:
Reference: https://docs.microsoft.com/en-us/learn/modules/secure-network-connectivity-azure/2-what-is-defense-in-depth
정답:
Explanation:
Firewall is really not directly protecting the Virtual Networks though DDOS would have been ideal for VNETS

정답: 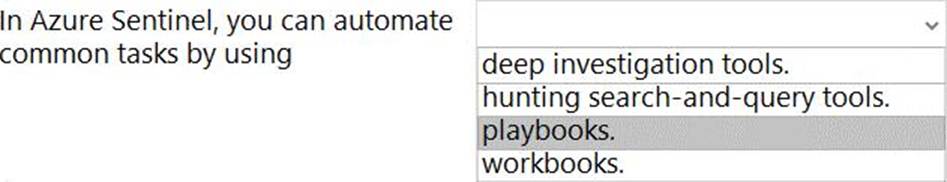
Explanation:
Reference: https://docs.microsoft.com/en-us/azure/sentinel/overview
정답:
Explanation:
Network protection helps protect devices from Internet-based events. Network protection is an attack surface reduction capability.
Reference: https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/network-protection?view=o365-worldwide