Fortinet NSE 4 - FortiOS 7.6 Administrator 온라인 연습
최종 업데이트 시간: 2025년11월17일
당신은 온라인 연습 문제를 통해 Fortinet NSE4_FGT_AD-7.6 시험지식에 대해 자신이 어떻게 알고 있는지 파악한 후 시험 참가 신청 여부를 결정할 수 있다.
시험을 100% 합격하고 시험 준비 시간을 35% 절약하기를 바라며 NSE4_FGT_AD-7.6 덤프 (최신 실제 시험 문제)를 사용 선택하여 현재 최신 296개의 시험 문제와 답을 포함하십시오.
정답:
Explanation:
The Dead Peer Detection (DPD) mode on FortiGate that will meet the requirement of sending DPD probes only when no traffic is observed in the tunnel is "On Idle."
Therefore, the correct answer is:
D. On Idle
Disabled:
DPD is turned off. No detection probes are sent.
On Demand:
DPD probes are sent when there is no traffic detected in the tunnel for a specified period.
Enabled:
DPD probes are sent periodically, regardless of whether there is traffic in the tunnel or not.
On Idle:
DPD probes are sent only when there is no traffic observed in the tunnel for a certain period. This mode is often preferred when you want to conserve bandwidth by sending DPD probes only when the tunnel is not actively transmitting data.
In the context of the administrator's requirement to send DPD probes only when no traffic is observed in the tunnel, the appropriate choice is "On Idle." This ensures that the DPD probes are triggered only during periods of inactivity, helping to detect and address potential issues in a more bandwidth-efficient manner.
정답:
Explanation:
The two inspection modes that you can use to configure a firewall policy on a profile-based next-generation firewall (NGFW) are:
A. Proxy-based inspection
Proxy-based inspection involves buffering and inspecting the entire content of the traffic before allowing
it through. It offers in-depth content analysis.
C. Flow-based inspection
Flow-based inspection involves inspecting the traffic based on predefined signatures and patterns
without buffering the entire content. It optimizes performance compared to proxy-based inspection.
So, the correct choices are A and C.
Profile based - Flow or proxy based.
Policy based - flow only.
정답:
Explanation:
The type of logs on FortiGate that records information about traffic directly to and from the FortiGate nmanagement IP addresses is:
A. Local traffic logs
Local traffic logs include information about traffic that is directed to and from the FortiGate unit itself, including traffic to and from the FortiGate management IP addresses. These logs provide details about communication involving the FortiGate device.
So, the correct choice is A.
정답:
Explanation:
The two correct statements regarding FortiGate FSSO agentless polling mode are:
B. FortiGate uses the SMB protocol to read the event viewer logs from the DCs.
In agentless polling mode, FortiGate uses the Server Message Block (SMB) protocol to access and read event viewer logs from the Domain Controllers (DCs).
D. FortiGate queries AD by using the LDAP to retrieve user group information.
In agentless polling mode, FortiGate queries Active Directory (AD) using the Lightweight Directory Access Protocol (LDAP) to retrieve user group information. So, the correct choices are B and D.
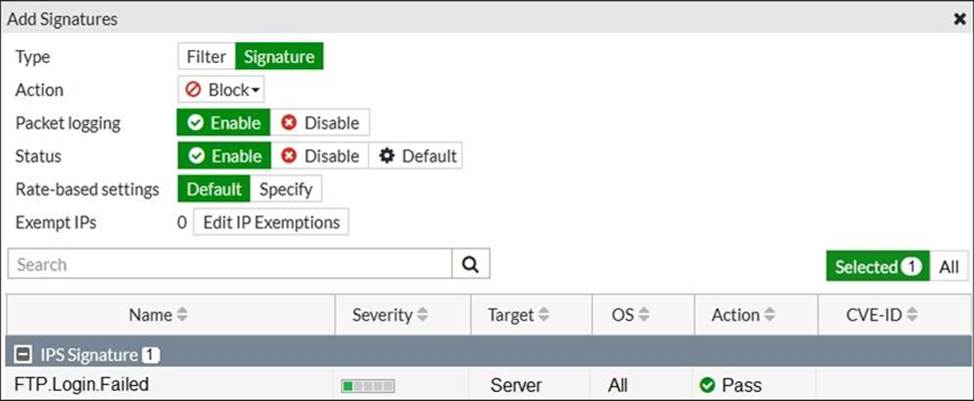
정답:
Explanation:
"pass" is only default action.
The Pass action on the specific signature would only be chosen, if the Action (on the top) was set to Default. But instead its set to Block, se the action is will be to block and drop.
Select Allow to allow traffic to continue to its destination. Select Monitor to allow traffic to continue to its destination and log the activity. Select Block to silently drop traffic matching any of the signatures included in the entry. Select Reset to generate a TCP RST packet whenever the signature is triggered. Select Default to use the default action of the signatures.
If you enable Packet logging, FortiGate saves a copy of the packet that matches the signature.
정답:
Explanation:
C: Operating mode is per-VDOM setting. You can combine transparent mode VDOM's with NAT mode VDOMs on the same physical Fortigate.
D: Inspection-mode selection has moved from VDOM to firewall policy, and the default inspection-mode is flow, so NGFW Mode can be changed from Profile-base (Default) to Policy-base directly in System > Settings from the VDOM.
A and B are incorrect: The firmware on your Fortigate and some settings, such as system time, apply to the entire device-they are not specific to each VDOM.
NGFW mode is a per-VDOM setting.
Operation mode is a per-VDOM setting. You can combine transparent mode VDOMs with NAT mode VDOMs on the same physical FortiGate.
정답:
Explanation:
The three remote log storage options you can configure on FortiGate are:
A. FortiSIEM
FortiSIEM is a comprehensive security information and event management (SIEM) solution that allows
for centralized log storage and analysis.
B. FortiCloud
FortiCloud provides cloud-based services, including log storage, for Fortinet devices, allowing for remote
log storage and management.
E. FortiAnalyzer
FortiAnalyzer is a dedicated log and analysis appliance that provides centralized log storage, reporting,
and analysis capabilities for Fortinet devices.
So, the correct choices are A, B, and E.
Fortisandbox is not a logging solution.
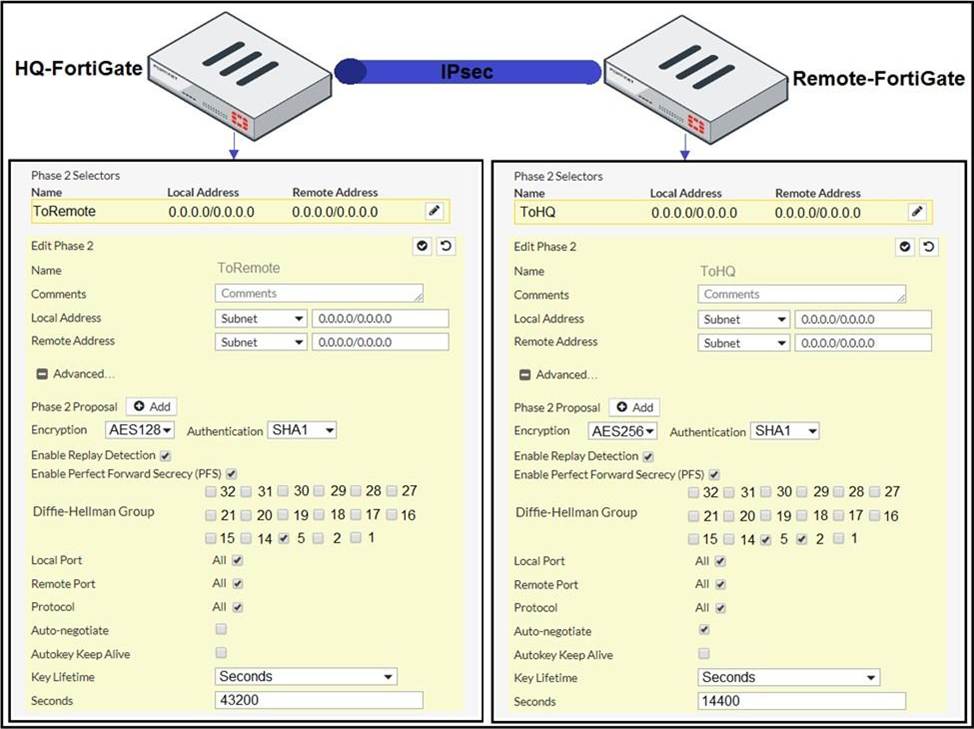
정답:
Explanation:
D. On HQ-FortiGate, set Encryption to AES256.
A phase 2 proposal defines the algorithms supported by the peer for encrypting and decrypting the data over the tunnel. You can configure multiple proposals to offer more options to the remote peer when negotiating the IPsec SAs.
Like in phase 1, you need to select a combination of encryption and authentication algorithms. D is correct, the Encryption and authentication algorithm needs to match inorder for IPSEC be successfully established Encryption algorithm must be the same.
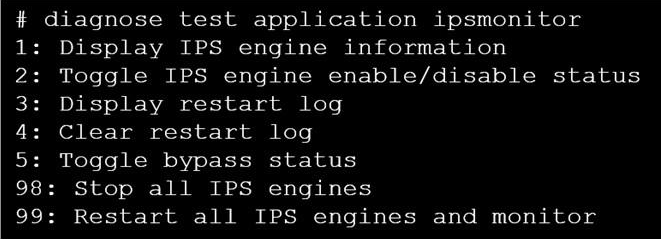
정답:
Explanation:
If there are high-CPU use problems caused by the IPS, you can use the diagnose test application ipsmonitor command with option 5 to isolate where the problem might be. Option 5 enables IPS bypass mode.
In this mode, the IPS engine is still running, but it is not inspecting traffic.
If the CPU use decreases after that, it usually indicates that the volume of traffic being inspected is too high for that FortiGate model.
If the CPU use remains high after enabling IPS bypass mode, it usually indicates a problem in the IPS engine, which you must report to Fortinet Support.
If there are high-CPU use problems caused by the IPS, you can use the diagnose test application ipsmonitor command with option 5 to isolate where the problem might be. Option 5 enables IPS bypass mode. In this mode, the IPS engine is still running, but it is not inspecting traffic. If the CPU use decreases after that, it usually indicates that the volume of traffic being inspected is too high for that FortiGate model.
정답:
Explanation:
정답:
Explanation:
B. The extreme database is available only on certain FortiGate models.
The Extreme database is available on certain FortiGate models and provides an even higher level of protection with additional signatures. It's designed for FortiGate models that support this extended feature set.
C. The extended database is available on all FortiGate models.
The Extended database is indeed available on all FortiGate models, providing additional signatures and detection capabilities beyond the normal database.
So, both statements B and C are accurate, with the understanding that the availability of the Extreme database is indeed limited to certain FortiGate models.
정답:
Explanation:
In a firewall policy set to proxy-based inspection mode:
B. The client must wait for the antivirus scan to finish scanning before it receives the file.
In proxy-based inspection, the client may need to wait for the antivirus scan to complete before receiving the file. The file may need to be fully scanned before being delivered to the client, depending on the specific configuration and circumstances.
D. If a virus is detected, a block replacement message is displayed immediately.
If a virus is detected during the antivirus scan in proxy-based inspection mode, FortiGate can generate a block replacement message immediately, informing the user that the file is infected. So, both statements B and D are valid in the context of proxy-based inspection mode.
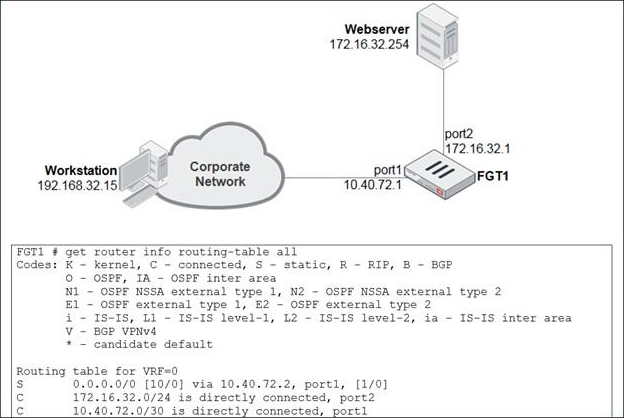
정답:
Explanation:
B. Loose RPF check will allow the traffic.
C. Strict RPF check will allow the traffic.
정답:
Explanation:
The three methods that can be used to deliver the token code to a user configured to use two-factor authentication are:
B. FortiToken
FortiToken is a physical or software-based token that generates time-based or event-based codes for two-factor authentication.
C. Email
The token code can be delivered to the user via email, where the user has access to the code through their email account.
E. SMS text message
The token code can be sent to the user as a text message (SMS) to their mobile device.
These methods provide flexibility in delivering the token code to users for two-factor authentication.
So, the correct choices are B, C, and E.
정답:
Explanation:
If the goal is to block the specific URL https://www.example.com/videos and allow all other URLs on the website, the correct configuration changes are:
B. Enable full SSL inspection.
Enabling full SSL inspection allows the FortiGate to inspect and filter HTTPS traffic, including the specific URL https://www.example.com/videos.
D. Configure a static URL filter entry for the URL and select Block as the action.
Create a static URL filter entry for the specific URL https://www.example.com/videos and set the action to Block. This will block access to the specified URL.
Enabling full SSL inspection is necessary to inspect and filter HTTPS traffic effectively, including the specific URL within the encrypted traffic.
So, the correct choices are B and D.