CompTIA Network+ Certification 온라인 연습
최종 업데이트 시간: 2025년11월17일
당신은 온라인 연습 문제를 통해 CompTIA N10-009 시험지식에 대해 자신이 어떻게 알고 있는지 파악한 후 시험 참가 신청 여부를 결정할 수 있다.
시험을 100% 합격하고 시험 준비 시간을 35% 절약하기를 바라며 N10-009 덤프 (최신 실제 시험 문제)를 사용 선택하여 현재 최신 107개의 시험 문제와 답을 포함하십시오.
정답:
Explanation:
GSM (Global System for Mobile communications) is the international standard that uses SIM cards to authenticate and connect phones to the cellular network. GSM allows users to place and receive calls while traveling globally, provided they have a SIM card. CDMA, on the other hand, does not use SIM cards in the same way and is primarily used in the United States. (Reference: CompTIA Network+ Study Guide, Chapter on Network Fundamentals)
정답:
Explanation:
LDAP over SSL (LDAPS) uses port 636 to provide secure, encrypted authentication for directory services.
Breakdown of Options:
A. SMTP (Simple Mail Transfer Protocol) C Uses port 25, not 636.
B. Syslog C Uses port 514 (UDP), not 636.
C. TFTP (Trivial File Transfer Protocol) C Uses port 69 (UDP), not 636.
D. LDAPS (Lightweight Directory Access Protocol Secure) C ✅ Correct answer. Uses port 636 for secure directory authentication.
Reference: CompTIA Network+ (N10-009) Official Study Guide C Domain 3.1: Compare and contrast network protocols.
RFC 4511: Lightweight Directory Access Protocol (LDAP)
정답:
Explanation:
Asymmetrical routing occurs when packets take different paths to and from the destination, leading to instability in network communication. The use of two different MPLS providers with OSPF can lead to this type of routing issue, especially if the paths aren't carefully configured and managed. This can cause unexpected routing behaviors and instability in a dual-WAN setup. (Reference: CompTIA Network+ Study Guide, Chapter on Network Routing)
정답:
Explanation:
Understanding Subnetting:
Original Network: 192.168.1.0/24 has a subnet mask of 255.255.255.0, which allows for 256 IP addresses (including network and broadcast addresses).
Objective: Divide this network into two equal subnets.
Calculating Subnet Mask:
New Subnet Mask: To divide 192.168.1.0/24 into two equal halves, we need to borrow one bit from the host portion of the address, changing the subnet mask to 255.255.255.128 (/25).
Subnet Breakdown:
First Subnet: 192.168.1.0/25 (192.168.1.0 - 192.168.1.127)
Second Subnet: 192.168.1.128/25 (192.168.1.128 - 192.168.1.255)
Verification:
Each subnet now has 128 IP addresses (126 usable IP addresses, excluding the network and broadcast addresses).
Comparison with Other Options:
정답:
Explanation:
If the IP phone works but the workstation doesn't, it indicates that the Voice VLAN is functioning correctly, but the Data VLAN (C) is either misconfigured or missing. The workstation typically connects through the phone, which tags voice and data traffic separately using VLANs. A. Voice VLAN is for the IP phone, which is already working.
B. Native VLAN is for untagged traffic on trunk ports, but doesn’t control access directly.
D. Trunk port is more relevant to switch interconnections than individual workstation ports.
Reference: CompTIA Network+ N10-009 Official Objectives: 2.3 C Given a scenario, configure and verify VLANs.
정답:
Explanation:
Introduction to Administrative Distance
Administrative distance (AD) is a value used by routers to rank routes from different routing protocols. AD represents the trustworthiness of the source of the route. Lower AD values are more preferred. If a router has multiple routes to a destination from different sources, it will choose the route with the lowest AD.
Static Routes and Backup Routes
When a dynamic routing protocol is not used, static routes can be employed. Static routes are manually configured routes. To ensure a backup route, multiple static routes to the same destination can be configured with different AD values.
Configuring Static Routes with Administrative Distance
The primary route is configured with a lower AD value, making it the preferred route. The backup route is configured with a higher AD value. In the event of the primary route failure, the router will then use the backup route.
Example Configuration:
plaintext
Copy code
ip route 192.168.1.0 255.255.255.0 10.0.0.1 1
ip route 192.168.1.0 255.255.255.0 10.0.0.2 10
In the above example, 192.168.1.0/24 is the destination network.
정답:
Explanation:
To support VoIP on the same physical ports used by computers:
B. Enable 802.1Q: This standard supports VLAN tagging, allowing voice and data traffic to share the same port using separate VLANs.
D. Set up voice VLANs: Separating voice traffic into its own VLAN improves QoS and manageability.
Other options are not directly related to configuring VoIP over existing ports:
A. Network translation definitions (NAT) are unrelated to switch-level VLAN configuration.
C. Routing protocols are not necessary at the switch level for VLAN setup.
E. DNS is not required for the switch or VLAN setup.
F. Perimeter network (DMZ) is used for public-facing servers, not VoIP VLANs.
Reference: CompTIA Network+ N10-009 Official Objectives: 2.3 C Given a scenario, configure and verify VLANs.
CompTIA Network+ N10-009 Official Objectives: 3.6 C Explain the characteristics of network topologies and types.
정답:
Explanation:
When installing multiple Power over Ethernet (PoE) devices like security cameras, it is crucial to ensure that the total power requirement does not exceed the power budget of the PoE switch. Each PoE switch has a maximum power capacity, and exceeding this capacity can cause some devices to fail to receive power.
PoE Standards: PoE switches conform to standards such as IEEE 802.3af (PoE) and 802.3at (PoE+), each with specific power limits per port and total power capacity.
Power Calculation: Adding up the power requirements of all connected PoE devices can help determine if the total power budget of the switch is exceeded.
Symptoms: When the power budget is exceeded, some devices, typically those farthest from the switch or connected last, may not power up or function correctly. Network
Reference: CompTIA Network+ N10-007 Official Certification Guide: Covers PoE standards and troubleshooting power issues.
Cisco Networking Academy: Discusses PoE technologies, power budgeting, and managing PoE devices.
Network+ Certification All-in-One Exam Guide: Provides information on PoE setup, including power budget considerations.
정답:
Explanation:
• Too much overlap on the same channel (all devices on channel 11) causes interference, leading to retransmissions and high latency.
• Same SSIDs (A) are expected in mesh networks.
• Device compatibility (C) would show different symptoms.
• Node power (D) affects coverage, not congestion.
Reference: CompTIA Network+ N10-009 Official Documentation C Wireless Troubleshooting & Signal Interference.
정답:
Explanation:
• Cable termination issues (e.g., improper crimping, loose connectors) can cause connectivity failures.
• Power budget (A) applies to PoE devices, not general cabling issues.
• Device requirements (B) relate to software/hardware compatibility, not wiring faults.
• Port status (C) would help if the issue was switch-related, but since moving devices didn’t help, it’s likely a cabling issue.
Reference: CompTIA Network+ N10-009 Official Documentation C Cabling & Physical Layer Troubleshooting.
정답:
Explanation:
An SLA (Service Level Agreement) defines performance expectations, including response time, prioritization, and resolution time for services and support issues. It helps the technician determine which task has higher priority based on business impact.
A. NDA (Non-Disclosure Agreement) relates to confidentiality, not task prioritization.
B. AUP (Acceptable Use Policy) defines user behavior, not issue handling.
D. MOU (Memorandum of Understanding) outlines informal agreements and doesn't define ticket priorities.
Reference: CompTIA Network+ N10-009 Official Objectives: 4.1 C Compare and contrast common documentation types.
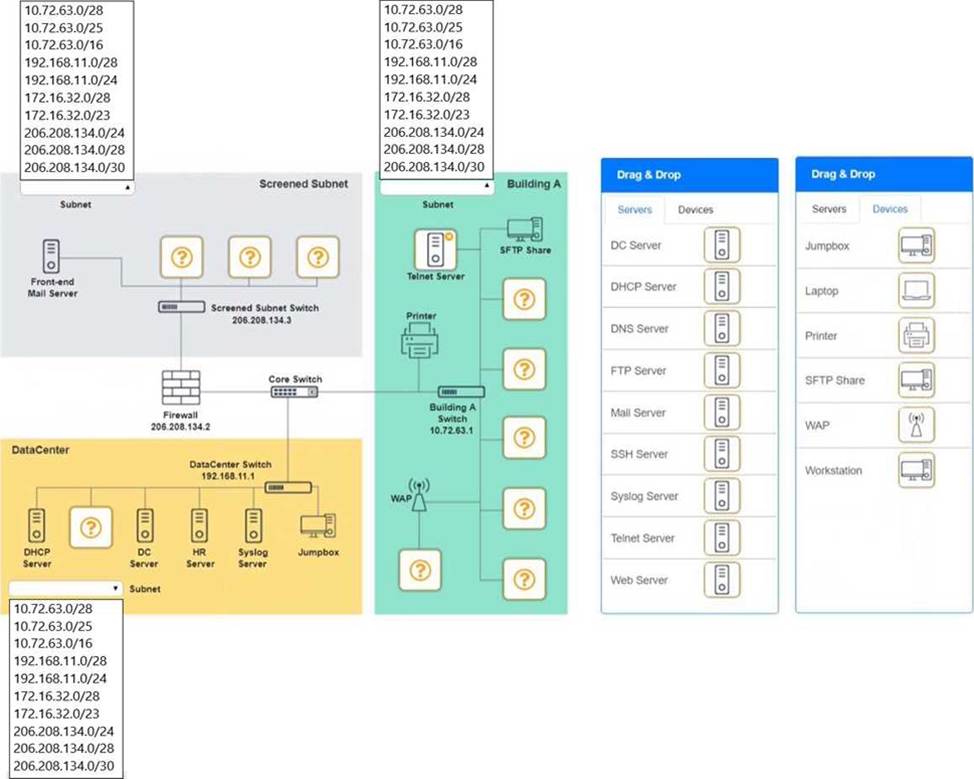
정답: Screened Subnet devices C Web server, FTP server
Building A devices C SSH server top left, workstations on all 5 on the right, laptop on bottom left DataCenter devices C DNS server.
A screenshot of a computer AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect. A screenshot of a computer AI-generated content may be incorrect.
정답:
Explanation:
VLAN hopping is an attack where an attacker crafts packets with multiple VLAN tags, allowing them to traverse VLAN boundaries improperly. This can result in gaining unauthorized access to network segments that are supposed to be isolated. The other options do not involve the use of multiple network tags. MAC flooding aims to overwhelm a switch’s MAC address table, DNS spoofing involves forging DNS responses, and ARP poisoning involves sending fake ARP messages.
Reference: According to the CompTIA Network+ course materials, VLAN hopping exploits the tagging mechanism in network packets to gain unauthorized access.
정답:
Explanation:
Port 587 is used for secure email submission. This port is designated for message submission by mail clients to mail servers using the SMTP protocol, typically with STARTTLS for encryption.
Port 25: Traditionally used for SMTP relay, but not secure and often blocked by ISPs for outgoing mail due to spam concerns.
Port 110: Used for POP3 (Post Office Protocol version 3), not typically secured.
Port 143: Used for IMAP (Internet Message Access Protocol), which can be secured with STARTTLS or SSL/TLS.
Port 587: Specifically used for authenticated email submission (SMTP) with encryption, ensuring secure transmission of email from clients to servers. Network
Reference: CompTIA Network+ N10-007 Official Certification Guide: Discusses email protocols and ports, including secure email transmission.
Cisco Networking Academy: Provides training on securing email communications and the use of appropriate ports.
Network+ Certification All-in-One Exam Guide: Explains email protocols, ports, and security considerations for email transmission.
정답:
Explanation:
Direct Connect refers to a dedicated network connection between an on-premises network and a cloud service provider (such as AWS Direct Connect). This link bypasses the public internet, providing a more reliable and higher-bandwidth connection. It may not inherently include encryption because it relies on the security measures of the dedicated physical connection itself. In contrast, other options like VPN typically involve encryption as they traverse the public internet.
Reference: CompTIA Network+ full course material indicates that Direct Connect type services offer dedicated, private connections which might not include encryption due to the dedicated and secure nature of the link itself.