Security, Specialist (JNCIS-SEC) 온라인 연습
최종 업데이트 시간: 2025년11월17일
당신은 온라인 연습 문제를 통해 Juniper JN0-336 시험지식에 대해 자신이 어떻게 알고 있는지 파악한 후 시험 참가 신청 여부를 결정할 수 있다.
시험을 100% 합격하고 시험 준비 시간을 35% 절약하기를 바라며 JN0-336 덤프 (최신 실제 시험 문제)를 사용 선택하여 현재 최신 103개의 시험 문제와 답을 포함하십시오.
정답:
Explanation:
You have exceeded the maximum files submission for your SRX platform size: This statement
is correct because file scanning on SRX300 Series device has a limit on the number of files that can be submitted per minute based on the platform size3. For example, SRX320 has a limit of 10 files per minute3.
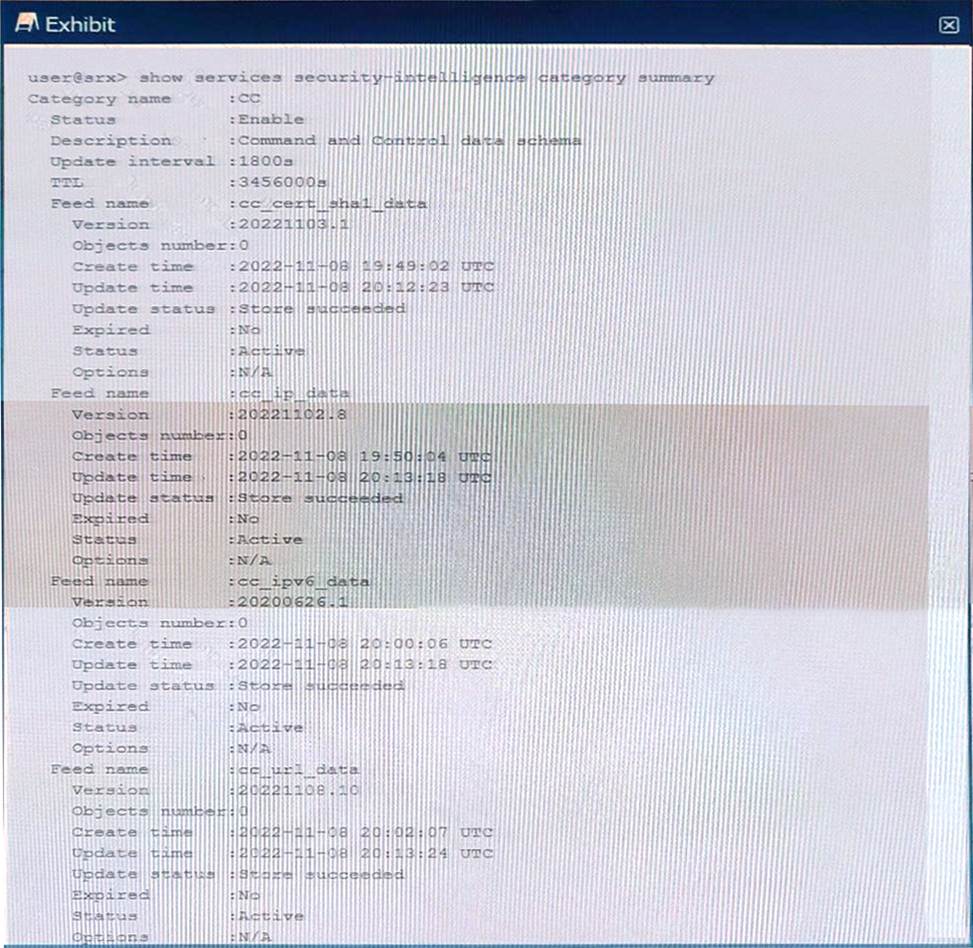
정답:
Explanation:
According to the Juniper Networks JNCIS-SEC Study Guide, when you set up your command-and-control (C&C) category with Juniper ATP Cloud, all of the feeds will initially have zero objects in them. This is normal, as it can take a few minutes for the feeds to download. No action is required in this scenario and you will notice the feeds start to populate with objects once the download is complete.
정답:
Explanation:
AppTrack is a feature of Juniper Networks firewall solutions that allows administrators to track applications, users, and the amount of traffic generated by those applications on the network. AppTrack can be enabled on specific security zones of the network to monitor traffic on those zones. This feature can be used to determine how much traffic a popular gaming application isgenerating on the network. For more information, please refer to the Juniper Networks JNCIS-SEC Study Guide.
정답:
Explanation:
You can specify the source IP address or a range of IP addresses to exclude certain traffic originating from specific network segments or devices. This is useful for whitelisting traffic from known, secure sources that are otherwise triggering false positives in the IPS system.
Similarly, you can specify the destination IP address or a range of addresses to exclude traffic destined for particular network hosts or segments. This helps in reducing false positives for traffic directed towards trusted internal resources or specific external services that are known to be safe.
정답:
정답:
Explanation:
When using SSL proxy, the servers themselves do not require any special configuration to utilize the SSL proxy function on the SRX device. The SSL proxy operates transparently, intercepting and decrypting SSL/TLS traffic before it reaches the servers.
For the SSL proxy to function effectively, especially in server protection mode where it impersonates the server to the client, it is necessary to load the server's certificates onto the SRX device. This allows the SRX to establish a trusted connection with the client using the server's credentials.
정답:
Explanation:
In a chassis cluster, both nodes can host active redundancy groups. The active redundancy groups can be distributed between the two nodes, depending on the configuration and failover status, allowing each node to handle traffic for different sets of services or interfaces.
For the chassis clustering to function correctly, both nodes in the cluster must be of the same model. This requirement ensures that the hardware capabilities, such as processing power and interface compatibility, are identical, which is crucial for maintaining consistent performance and behavior between cluster nodes.
정답:
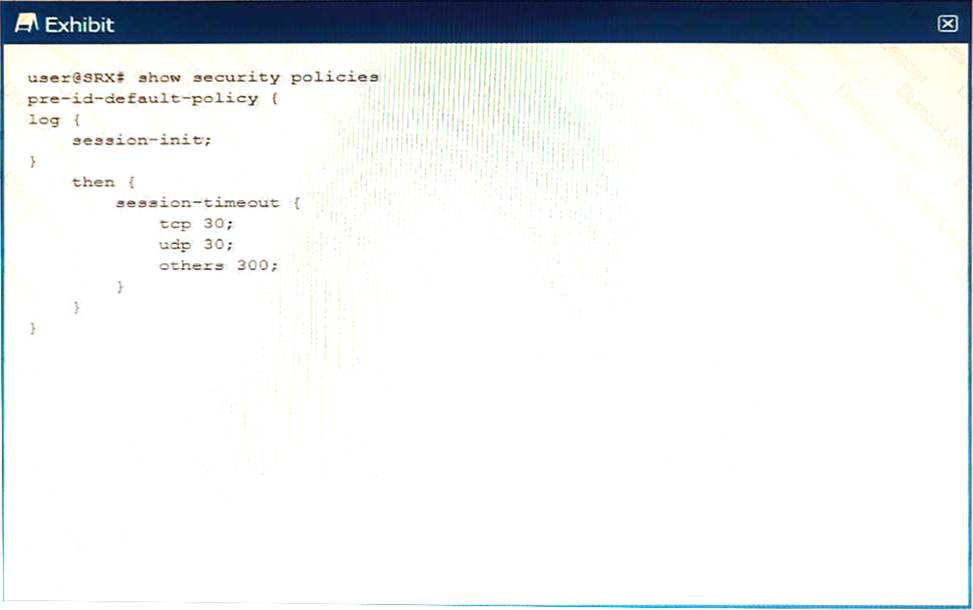
정답:
Explanation:
The log session-init; command within the policy configuration specifies that an event log entry will be created every time a session is initialized, meaning each new session will generate a log event. This is useful for tracking and analyzing the traffic flows entering the device.
Changing session-init to session-close in the log statement would mean that the device logs sessions when they close instead of when they open. This setting is typically used to log details about the session upon termination, which can help in analyzing the duration, end status, and other parameters of sessions, including those of unidentified flows.
정답:
Explanation:
Juniper Identity Management Service (JIMS) domain PC probes are used to map usernames to IP addresses in the domain security event log. This allows for the SRX Series device to verify authentication table information, such as group membership. The probes are triggered whenever a username to IP address mapping is not found in the domain security event log. By default, the probes are executed at 60-minute intervals.
정답:
정답:
Explanation:
vSRX provides flexible networking capabilities which include support for both Layer 2 (data link) and Layer 3 (network) configurations. This allows it to handle a variety of routing and switching tasks within virtual environments.
Clustering capability, which involves grouping multiple vSRX instances to operate as a single entity for redundancy and high availability, is a feature specific to vSRX. This is critical in environments where continuous uptime and resilience are required.
정답:
Explanation:
A single vSRX instance is capable of handling both firewall and NAT services simultaneously. This solution provides a streamlined and resource-efficient way to secure and manage network traffic within a private cloud environment.
Similar to the vSRX, a single cSRX can also provide both firewall and NAT services. The cSRX, being a containerized version of the SRX, is particularly suited for environments where high density and microservices architectures are used, offering high performance in a compact form factor.
정답:
Explanation:
Encrypted traffic insights (ETI) uses domain names to notify SRX Series devices about known malware sites. ETI is a feature of the SRX Series firewall that can detect and block malware that is hidden in encrypted traffic. It works by analyzing the domain names of the websites that the encrypted traffic is attempting to access. If the domain name matches a known malware site, ETIwill send an alert to the SRX Series device, which can then take appropriate action to block the traffic. ETI is a useful tool for protecting against threats that attempt to evade detection by hiding in encrypted traffic.
정답: