Palo Alto Networks XSIAM Engineer 온라인 연습
최종 업데이트 시간: 2025년10월10일
당신은 온라인 연습 문제를 통해 Paloalto Networks XSIAM Engineer 시험지식에 대해 자신이 어떻게 알고 있는지 파악한 후 시험 참가 신청 여부를 결정할 수 있다.
시험을 100% 합격하고 시험 준비 시간을 35% 절약하기를 바라며 XSIAM Engineer 덤프 (최신 실제 시험 문제)를 사용 선택하여 현재 최신 59개의 시험 문제와 답을 포함하십시오.
정답:
Explanation:
The most secure approach is to create a Disable Prevention Rule via Exceptions Configuration, scoped specifically to the Exceptions-AppServers profile. This rule should include the hash (SHA256), signer (Microsoft Corporation), and file path (C:\Windows\System32\cmd.exe). This ensures the exception is applied only to the trusted, legitimate process on the AppServers group while minimizing the security gap.
정답:
Explanation:
The correct command is cytool import suex -path </local/file/path>, which imports a supplied support exception (suex) file onto a Linux endpoint, ensuring the exception is applied locally.
정답:
Explanation:
The URL https://<region>-docker.pkg.dev is used in Palo Alto Networks infrastructure to download Engine Docker containers. This ensures the Cortex XSIAM engine components are pulled securely from the regional Docker registry.
정답:
Explanation:
To restore the content pack to its previously installed version, the engineer can directly reinstall the desired version from the Cortex Marketplace. Content packs support version management, allowing rollback or upgrade without requiring support intervention or removing existing configurations.
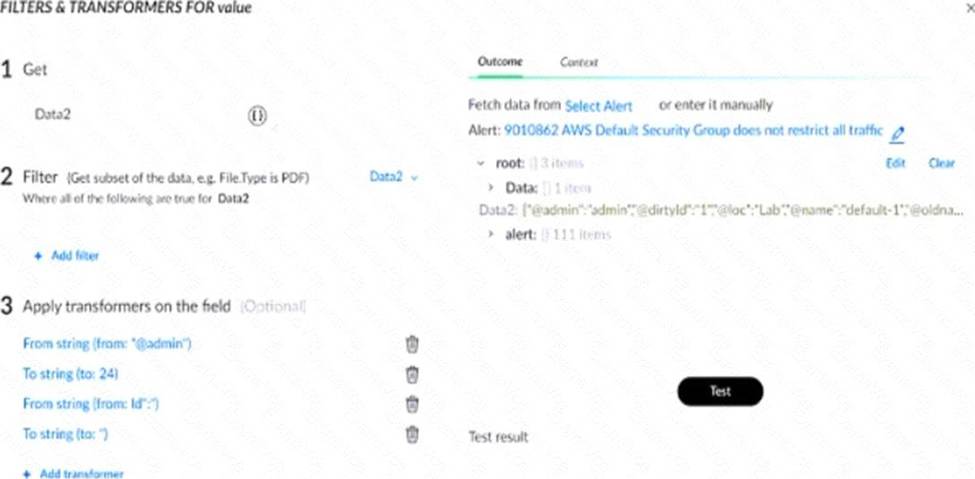
정답:
Explanation:
The applied transformers extract the value of @dirtyId from the root-level Data2 object. The sequence includes trimming using "Id:" and ending with a quotation mark ". As a result, the root @dirtyId value (1) is returned with a leading quotation mark, so the Test result will display "1.
정답:
Explanation:
Correlation rule errors can be tracked in XDR Collector audit logs (type = Rules, subtype = Error) and by querying the correlations_auditing dataset through XQL. These provide visibility into execution issues and failures for correlation rules.
정답:
Explanation:
For upgrading a non-Linux Kubernetes cluster, the correct installer type is Helm, since Helm charts are the supported method for deploying and managing Cortex XDR agents in Kubernetes environments.
정답:
Explanation:
When creating a custom incident domain in Cortex XSIAM, alert grouping still applies, allowing related alerts to be combined into incidents. However, SmartScore is not applied, since it is reserved for predefined domains.




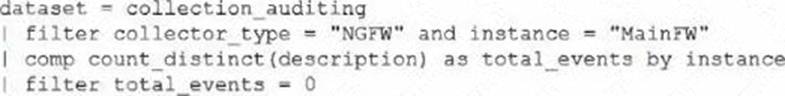
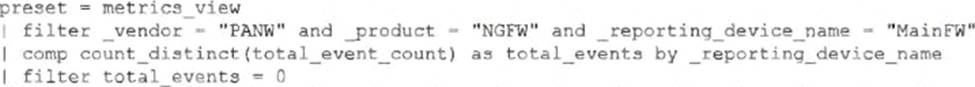


정답:
Explanation:
The correct query is the one using preset = metrics_view with comp sum(total_event_count) as total_events by _reporting_device_name and filtering total_events = 0.
This query directly checks event counts reported by the NGFW ("MainFW"). If no logs are received in the last 30 minutes, the total event count will be 0, which triggers the correlation rule alert.
정답:
Explanation:
Rolling tokens in Cortex XDR are used to perform administration on agents without relying on static credentials. This improves security by providing time-limited, automatically rotating tokens that maintain agent management access without exposing long-lived credentials.
정답:
Explanation:
A sudden data ingestion loss for a previously successful data source commonly occurs when the API key used for the integration has expired, breaking authentication and preventing further log collection.
정답:
Explanation:
Setting the "--memory-swap" option to "-1" during Cortex XSIAM engine deployment configures the container to run without requiring swap capabilities. This ensures the engine operates fully within allocated RAM, improving stability and avoiding issues related to memory swapping.
정답:
Explanation:
In the query action_local_port in (1122, 2234), the word "in" functions as an operator. It checks whether the field action_local_port matches any value in the specified list (1122, 2234).
정답:
Explanation:
The best approach is to minimize data modifications during ingestion, prioritizing raw data capture to preserve accuracy. Then, apply XDM (XSIAM Data Model) transformations and integrity checks post-ingestion. This ensures that threat detection and response are based on unaltered, high-fidelity data while still enabling normalization and enrichment after ingestion.
정답:
Explanation:
To prevent Cortex XSIAM from automatically extracting indicators (like IPs, domains, and URLs) from a script’s output, you must use 'AutoExtract': False in the script. This disables the auto-extraction mechanism for that script.