Palo Alto Networks Security Service Edge Engineer 온라인 연습
최종 업데이트 시간: 2025년10월10일
당신은 온라인 연습 문제를 통해 Paloalto Networks SSE Engineer 시험지식에 대해 자신이 어떻게 알고 있는지 파악한 후 시험 참가 신청 여부를 결정할 수 있다.
시험을 100% 합격하고 시험 준비 시간을 35% 절약하기를 바라며 SSE Engineer 덤프 (최신 실제 시험 문제)를 사용 선택하여 현재 최신 80개의 시험 문제와 답을 포함하십시오.
정답:
Explanation:
For complete data visibility in Prisma Access (Managed by Panorama), log forwarding profiles must be applied to all security policies to ensure that traffic logs are correctly sent to Strata Logging Service. If log forwarding is missing or misconfigured, some traffic data may not appear in the Application Command Center (ACC), leading to incomplete insights. Verifying and correctly assigning log forwarding ensures that all relevant network activity is captured and available for analysis.
정답:
Explanation:
When onboarding a new branch office to an existing IPSec termination node in Prisma Access, the QoS bandwidth is not automatically assigned. Instead, the newly added branch remains unallocated until the administrator manually assigns bandwidth within the QoS configuration settings. This ensures that customized bandwidth per site remains intact and allows for fine-tuned traffic management based on business needs.
정답:
Explanation:
When multitenancy is enabled in Prisma Access (Managed by Panorama), a key characteristic is the isolation of resources between tenants. Palo Alto Networks documentation emphasizes that each tenant operates within its own logically separate Prisma Access environment. This includes dedicated compute instances, ensuring that the performance and security of one tenant are not impacted by the activities of another.
Let's analyze why the other options are incorrect based on official documentation:
A. Service connection licenses will be assigned only to the first tenant, and these service connections can be shared with the other tenants. This statement is incorrect. In a multitenant Prisma Access deployment, licenses are typically managed and allocated per tenant. While the underlying infrastructure might be shared by Palo Alto Networks, the logical resources and often the licensing are segmented for each tenant. Sharing service connections across completely separate tenants would violate the principle of tenant isolation.
B. A single tenant cannot consist solely of mobile users or solely of remote networks. This statement is incorrect. Prisma Access multitenancy allows for flexibility in how tenants are configured. A tenant can be designed to exclusively serve mobile users, exclusively connect remote networks, or a combination of both, depending on the organizational structure and requirements.
D. There is flexibility to manage different tenants using separate Panoramas, which allows for better organization and management of the multiple tenants. While it is possible to have multiple Panorama instances managing different parts of a large infrastructure, when discussing multitenancy within a single Prisma Access instance (as implied by the question "enabling multitenancy in Prisma Access (Managed by Panorama))", all configured tenants are managed by that single Panorama instance. Managing different tenants with separate Panoramas is a different architectural consideration, not a defining characteristic of enabling multitenancy within one Prisma Access deployment managed by a specific Panorama.
Therefore, the defining characteristic of Prisma Access multitenancy (Managed by Panorama) is the allocation of dedicated Prisma Access instances and compute resources for each tenant, ensuring logical separation and resource isolation
정답:
Explanation:
When a large branch office experiences a high volume of employees logging in within a short time frame, the following apply:
Maximum pending TCP DNS requests is 64 C This means that Prisma Access can queue up to 64 pending DNS requests over TCP before dropping additional requests. If more requests are received simultaneously, some may fail or experience delays.
Maximum number of TCP DNS retries is 3 C If a DNS request fails over TCP, Prisma Access will attempt to retry the request up to three times before failing over to another method or returning an error.
정답:
Explanation:
To enable App Acceleration for SaaS applications in Prisma Access, the following configurations must be enabled:
Trusted Root CA for the CA certificate ensures that Prisma Access can validate and trust the SaaS application's certificates, allowing seamless inspection and acceleration of traffic without security warnings.
Forward Trust Certificate for the CA certificate enables SSL decryption for SaaS applications, allowing Prisma Access to optimize traffic and apply acceleration techniques while maintaining security policies.
정답:
Explanation:
In Prisma Access, configuring a notification profile allows engineers to receive alerts when IPSec tunnels experience downtime or instability. By defining specific conditions for remote network IPSec tunnels, the notification profile ensures that the engineer is proactively informed about tunnel failures, flapping, or degraded performance. This approach enables timely troubleshooting and minimizes disruptions for users relying on the IPSec tunnels.
정답:
Explanation:
When terminating a Partner Interconnect-based Colo-Connect in Prisma Access, the Customer Premises Equipment (CPE) must support IPSec as the overlay protocol. Prisma Access establishes secure IPSec tunnels between the Colo-Connect infrastructure and the CPE, ensuring encrypted communication and reliable connectivity. IPSec provides secure site-to-cloud integration, enabling customers to extend their private network securely over the Prisma Access infrastructure.
정답:
Explanation:
Updating the Cloud Services plugin in Prisma Access does not disrupt existing traffic flows because the upgrade process is designed to be seamless and transparent. Prisma Access ensures high availability by maintaining active sessions and policies while applying the update in the background. This allows ongoing connections to continue without interruptions, minimizing impact on user experience.
정답:
Explanation:
In Prisma Access, security policies are evaluated based on their configuration scope. If the engineer configured a Security policy under the Remote Networks scope, but traffic from the branch locations is instead matching a Security policy under the Prisma Access configuration scope, the intended policy will not take effect. This happens because Prisma Access evaluates security rules based on the highest-level applicable configuration first, which can override more specific Remote Networks policies.
정답:
Explanation:
In a multitenant deployment, access control must be configured at the Child Tenant level to ensure that security administrators have full control over Security policy only within their assigned tenant while restricting access to other tenants. By selecting Prisma Access & NGFW Configuration, the assigned users gain full administrative access only for security policy management within the designated tenant, aligning with RBAC best practices for controlled access in Prisma Access Managed by Strata Cloud Manager.
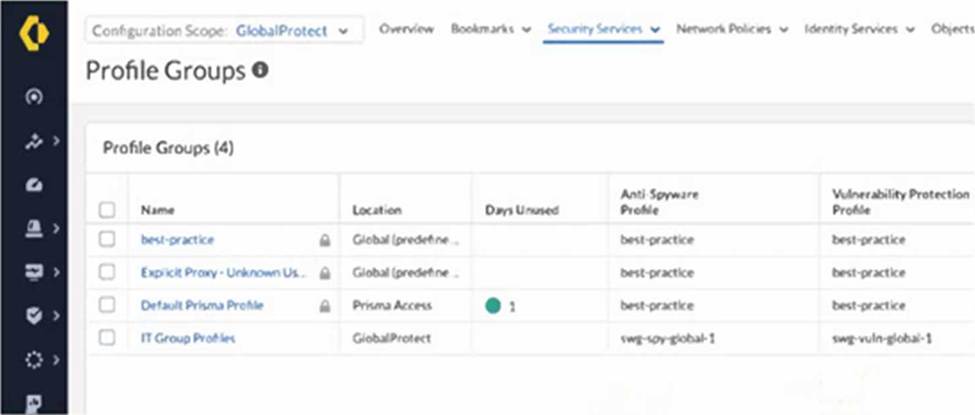
정답:
Explanation:
Palo Alto Networks best practices and the behavior of Strata Cloud Manager (SCM) dictate that predefined or default objects, including profile groups like "Default Prisma Profile," cannot be directly modified. These default objects serve as baseline configurations and are often locked to prevent accidental or unintended changes that could impact the overall security posture.
The intern's experience of the options being greyed out when selecting "Default Prisma Profile" is a direct indication of this immutability of default objects. Therefore, the correct action is to:
Create a new Profile Group: The intern should create a new profile group within the appropriate configuration scope (likely GlobalProtect, given the task).
Configure the new Profile Group: In this new profile group, the intern can select the desired Anti-Spyware Profile (which might be an existing custom profile or a new one they create).
Modify Security Rules: The security rules currently using the "Default Prisma Profile" in the GlobalProtect folder need to be modified to use this newly created profile group. Let's analyze why the other options are incorrect based on official documentation:
A. Request edit access for the GlobalProtect scope. While having the correct scope permissions is necessary for making any changes within GlobalProtect, it will not override the inherent immutability of default objects like "Default Prisma Profile." Edit access will allow the intern to create new objects and modify rules, but not directly edit the default profile group.
B. Change the configuration scope to Prisma Access and modify the profile group. The image shows that "Default Prisma Profile" has a "Location" of "Prisma Access." However, even within the Prisma Access scope, default profile groups are generally not directly editable. The issue is not the scope but the fact that it's a default object.
D. Modify the existing anti-spyware profile, because best-practice profiles cannot be removed from a
group. The question is about changing the profile group, not the individual Anti-Spyware Profile. While "best-practice" profiles might be part of default groups, the core issue is the inability to modify the default group itself. Creating a new group allows the intern to choose which Anti-Spyware Profile to include.
In summary, the fundamental principle in Palo Alto Networks management is that default objects are typically read-only to ensure a consistent and predictable baseline. To make changes, you need to create custom objects.
정답:
Explanation:
When the "Overlapping Subnets" checkbox is selected during the Remote Network onboarding process in Prisma Access, the deployment enables Private Application access using Prisma Access for Users (ZTNA or Private Access). This feature is designed to handle scenarios where multiple sites use the same IP subnet by leveraging NAT (Network Address Translation) and segmentation to avoid conflicts.
Since overlapping subnets can create routing challenges for direct remote network-to-remote network communication, Prisma Access does not support Remote Network-to-Remote Network or Mobile User communication in this case. Private application access is supported as Prisma Access correctly routes requests based on application-layer intelligence rather than IP-based routing.
정답:
Explanation:
The Strata Logging Service allows log replay, which enables resending logs that were not successfully forwarded to an external syslog server due to disruptions. By configuring a replay profile with the
affected time range and associating it with the syslog server profile, Prisma Access will resend the missing logs, ensuring that all relevant data is restored in the external logging system. This approach is the most efficient and automated way to recover missing logs.
정답:
Explanation:
Embargo rules in Prisma Access are designed to block traffic from specific countries that are subject to regulatory or policy-based restrictions. These rules help organizations enforce compliance by preventing inbound and outbound connections to or from regions that may pose security risks or are restricted due to legal or geopolitical reasons. They are commonly used to align with government sanctions and corporate security policies.
정답:
Explanation:
Ensuring that the Remote_Network_Template is selected when adding the User-ID Agent in Panorama is crucial because User-ID information must be associated with the correct Remote Network configuration for policies to apply properly. Additionally, the Service_Conn_Template must be selected when adding the User-ID Agent in Panorama, as the service connection is responsible for distributing User-ID mappings between the on-premises firewall and Prisma Access. If either of these configurations is incorrect, the user information will not be properly mapped, and traffic will not match user-based policies.