CompTIA SecurityX Certification Exam 온라인 연습
최종 업데이트 시간: 2025년10월10일
당신은 온라인 연습 문제를 통해 CompTIA CAS-005 시험지식에 대해 자신이 어떻게 알고 있는지 파악한 후 시험 참가 신청 여부를 결정할 수 있다.
시험을 100% 합격하고 시험 준비 시간을 35% 절약하기를 바라며 CAS-005 덤프 (최신 실제 시험 문제)를 사용 선택하여 현재 최신 117개의 시험 문제와 답을 포함하십시오.
정답:
Explanation:
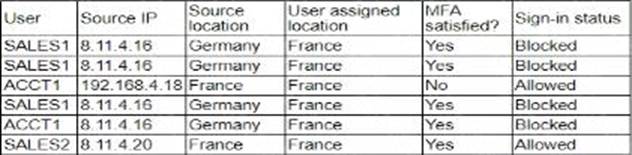
The table shows that the user "SALES1" is consistently blocked despite having met the MFA requirements. The common factor in these blocked attempts is the source IP address (8.11.4.16) being identified as from Germany while the user is assigned to France. This discrepancy suggests that the network geolocation is being misidentified by the authentication server, causing legitimate access attempts to be blocked.
Why Network Geolocation Misidentification?
Geolocation Accuracy: Authentication systems often use IP geolocation to verify the location of access attempts. Incorrect geolocation data can lead to legitimate requests being denied if they appear to come from unexpected locations.
Security Policies: Company security policies might block access attempts from certain locations to prevent unauthorized access. If the geolocation is wrong, legitimate users can be inadvertently blocked.
Consistent Pattern: The user "SALES1" from the IP address 8.11.4.16 is always blocked, indicating a consistent issue with geolocation.
Other options do not align with the pattern observed:
A. Bypass MFA requirements: MFA is satisfied, so bypassing MFA is not the issue.
C. Administrator access policy: This is about user access, not specific administrator access.
D. OTP codes: The user has satisfied MFA, so OTP code configuration is not the issue.
Reference: CompTIA SecurityX Study Guide
"Geolocation and Authentication," NIST Special Publication 800-63B
"IP Geolocation Accuracy," Cisco Documentation
정답:
Explanation:
To meet the requirements of only allowing internally signed applications, preventing unauthorized software installations, and logging attempts to run unauthorized software, configuring application control with blocked hashes and enterprise-trusted root certificates is the best solution. This approach ensures that only applications signed by trusted certificates are allowed to execute, while all other attempts are blocked and logged. It effectively prevents unauthorized software installations by restricting execution to pre-approved applications.
Reference: CompTIA SecurityX Study Guide: Describes application control mechanisms and the use of trusted certificates to enforce security policies.
NIST Special Publication 800-53, "Security and Privacy Controls for Information Systems and
Organizations": Recommends application whitelisting and execution control for securing endpoints. "The Application Security Handbook" by Mark Dowd, John McDonald, and Justin Schuh: Covers best practices for implementing application control and managing trusted certificates
정답:
Explanation:
The most secure way to prevent inadvertent data disclosure when encrypted SSDs are reused is to securely delete the encryption keys used by the SSD. Without the encryption keys, the data on the SSD remains encrypted and is effectively unreadable, rendering any residual data useless. This method is more reliable and efficient than overwriting data multiple times or using other physical destruction methods.
Reference: CompTIA SecurityX Study Guide: Highlights the importance of managing encryption keys and securely deleting them to protect data.
NIST Special Publication 800-88, "Guidelines for Media Sanitization": Recommends cryptographic erasure as a secure method for sanitizing encrypted storage devices.
정답:
Explanation:
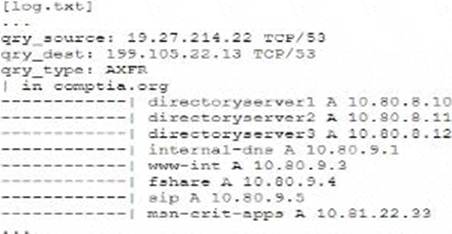
The log snippet indicates a DNS AXFR (zone transfer) request, which can be exploited by attackers to gather detailed information about an internal network's infrastructure. Disabling DNS zone transfers is the best solution to mitigate this risk. Zone transfers should generally be restricted to authorized secondary DNS servers and not be publicly accessible, as they can reveal sensitive network information that facilitates lateral movement during an attack.
Reference: CompTIA SecurityX Study Guide: Discusses the importance of securing DNS configurations, including restricting zone transfers.
NIST Special Publication 800-81, "Secure Domain Name System (DNS) Deployment Guide":
Recommends restricting or disabling DNS zone transfers to prevent information leakage.
정답:
Explanation:
The most likely cause of the anti-malware alerts on customer workstations is unsecure bundled libraries. When developing and deploying new applications, it is common for developers to use third-party libraries. If these libraries are not properly vetted for security, they can introduce vulnerabilities or malicious code.
Why Unsecure Bundled Libraries?
Third-Party Risks: Using libraries that are not secure can lead to malware infections if the libraries contain malicious code or vulnerabilities.
Code Dependencies: Libraries may have dependencies that are not secure, leading to potential security risks.
Common Issue: This is a frequent issue in software development where libraries are used for convenience but not properly vetted for security.
Other options, while relevant, are less likely to cause widespread anti-malware alerts:
A. Misconfigured code commit: Could lead to issues but less likely to trigger anti-malware alerts.
C. Invalid code signing certificate: Would lead to trust issues but not typically anti-malware alerts.
D. Data leakage: Relevant for privacy concerns but not directly related to anti-malware alerts.
Reference: CompTIA SecurityX Study Guide
"Securing Open Source Libraries," OWASP
"Managing Third-Party Software Security Risks," Gartner Research
정답:
Explanation:
Creating a separate network for users who need access to the application is the best action to secure an internal application that is critical to the production area and cannot be updated.
Why Separate Network?
Network Segmentation: Isolates the critical application from the rest of the network, reducing the risk of compromise and limiting the potential impact of any security incidents.
Controlled Access: Ensures that only authorized users have access to the application, enhancing security and reducing the attack surface.
Minimized Risk: Segmentation helps in protecting the application from vulnerabilities that could be exploited from other parts of the network.
Other options, while beneficial, do not provide the same level of security for a critical application:
A. Disallow wireless access: Useful but does not provide comprehensive protection.
B. Deploy intrusion detection capabilities using a network tap: Enhances monitoring but does not
provide the same level of isolation and control.
C. Create an acceptable use policy: Important for governance but does not provide technical security
controls.
Reference: CompTIA SecurityX Study Guide
NIST Special Publication 800-125, "Guide to Security for Full Virtualization Technologies"
"Network Segmentation Best Practices," Cisco Documentation
정답:
Explanation:
The most likely reason the device must be replaced is that the motherboard was not configured with a TPM (Trusted Platform Module) from the OEM (Original Equipment Manufacturer) supplier.
Why TPM is Necessary for Full Disk Encryption:
Hardware-Based Security: TPM provides a hardware-based mechanism to store encryption keys securely, which is essential for full disk encryption.
Compatibility: Full disk encryption solutions, such as BitLocker, require TPM to ensure that the encryption keys are securely stored and managed.
Integrity Checks: TPM enables system integrity checks during boot, ensuring that the device has not been tampered with.
Other options do not directly address the requirement for TPM in supporting full disk encryption:
A. The HSM is outdated: While HSM (Hardware Security Module) is important for security, it is not typically used for full disk encryption.
B. The vTPM was not properly initialized: vTPM (virtual TPM) is less common and not typically a reason for requiring hardware replacement.
C. The HSM is vulnerable to common exploits: This would require a firmware upgrade, not replacement of the device.
E. The HSM does not support sealing storage: Sealing storage is relevant but not the primary reason
for requiring TPM for full disk encryption.
Reference: CompTIA SecurityX Study Guide
"Trusted Platform Module (TPM) Overview," Microsoft Documentation "BitLocker Deployment Guide," Microsoft Documentation
정답:
Explanation:
To reduce the risk of unauthorized BYOD (Bring Your Own Device) usage, the organization should implement Conditional Access and Network Access Control (NAC).
Why Conditional Access and NAC?
Conditional Access:
User-to-Device Binding: Conditional access policies can enforce that only registered and compliant devices are allowed to access corporate resources.
Context-Aware Security: Enforces access controls based on the context of the access attempt, such as user identity, device compliance, location, and more. Network Access Control (NAC):
Device Configuration Requirements: NAC ensures that only devices meeting specific security configurations are allowed to connect to the network.
Access Control: Provides granular control over network access, ensuring that BYOD devices comply with security policies before gaining access.
Other options, while useful, do not address the specific need to control and secure BYOD devices effectively:
A. Cloud IAM to enforce token-based MFA: Enhances authentication security but does not control device compliance.
D. PAM to enforce local password policies: Focuses on privileged account management, not BYOD control.
E. SD-WAN to enforce web content filtering: Enhances network performance and security but does not enforce BYOD device compliance.
F. DLP to enforce data protection capabilities: Protects data but does not control BYOD device access
and compliance.
Reference: CompTIA SecurityX Study Guide
"Conditional Access Policies," Microsoft Documentation
"Network Access Control (NAC)," Cisco Documentation
정답:
Explanation:
To provide secure access to internal and external cloud resources, eliminate split-tunnel traffic flows, and enable identity and access management capabilities, the most appropriate solutions are CASB (Cloud Access Security Broker) and SASE (Secure Access Service Edge).
Why CASB and SASE?
CASB (Cloud Access Security Broker):
Secure Access: CASB solutions provide secure access to cloud resources by enforcing security policies and monitoring user activities.
Identity and Access Management: CASBs integrate with identity and access management (IAM)
systems to ensure that only authorized users can access cloud resources.
Visibility and Control: They offer visibility into cloud application usage and control over data sharing and access.
SASE (Secure Access Service Edge):
Eliminate Split-Tunnel Traffic: SASE integrates network security functions with WAN capabilities to ensure secure access without the need for split-tunnel configurations.
Comprehensive Security: SASE provides a holistic security approach, including secure web gateways, firewalls, and zero trust network access (ZTNA).
Identity-Based Access: SASE leverages IAM to enforce access controls based on user identity and context.
Other options, while useful, do not comprehensively address all the requirements:
A. Federation: Useful for identity management but does not eliminate split-tunnel traffic or provide comprehensive security.
B. Microsegmentation: Enhances security within the network but does not directly address secure access to cloud resources or split-tunnel traffic.
D. PAM (Privileged Access Management): Focuses on managing privileged accounts and does not provide comprehensive access control for internal and external resources.
E. SD-WAN: Enhances WAN performance but does not inherently provide the identity and access management capabilities or eliminate split-tunnel traffic.
Reference: CompTIA SecurityX Study Guide
"CASB: Cloud Access Security Broker," Gartner Research
정답:
Explanation:
A Configuration Management Database (CMDB) provides the best foundation for identifying which specific assets are affected by a given vulnerability. A CMDB maintains detailed information about the IT environment, including hardware, software, configurations, and relationships between assets.
This comprehensive view allows organizations to quickly identify and address vulnerabilities affecting specific assets.
Reference: CompTIA SecurityX Study Guide: Discusses the role of CMDBs in asset management and vulnerability identification.
ITIL (Information Technology Infrastructure Library) Framework: Recommends the use of CMDBs for effective configuration and asset management.
"Configuration Management Best Practices" by Bob Aiello and Leslie Sachs: Covers the importance of CMDBs in managing IT assets and addressing vulnerabilities.
정답:
Explanation:
The General Data Protection Regulation (GDPR) is the regulation most likely being addressed by the news organization. GDPR includes provisions for the "right to be forgotten," which allows individuals to request the deletion of personal data that is no longer necessary for the purposes for which it was collected. This regulation aims to protect the privacy and personal data of individuals within the European Union.
Reference: CompTIA SecurityX Study Guide: Covers GDPR and its requirements, including the right to be forgotten.
GDPR official documentation: Details the rights of individuals, including data erasure and the right to beforgotten.
"GDPR: A Practical Guide to the General Data Protection Regulation" by IT Governance Privacy Team: Provides a comprehensive overview of GDPR compliance, including workflows for data deletion requests.
정답:
Explanation:
To secure the Operational Technology (OT) environment based on the given requirements, the best approach is to implement a bastion host in the OT network. The bastion host serves as a secure entry point for remote access, allowing third-party vendors to connect while being monitored by security tools. Using a dedicated update server for workstations ensures that security updates are applied in a controlled manner without direct internet access.
Reference: CompTIA SecurityX Study Guide: Recommends the use of bastion hosts and dedicated update servers for securing OT environments.
NIST Special Publication 800-82, "Guide to Industrial Control Systems (ICS) Security": Advises on
isolating OT networks and using secure remote access methods.
"Industrial Network Security" by Eric
D. Knapp and Joel Thomas Langill: Discusses strategies for securing OT networks, including the use of bastion hosts and update servers.
정답:
Explanation:
To improve the quality of code scanning results and reduce false positives, the best solution is to limit the tool to a specific coding language and fine-tune the rule set. By configuring the code scanning tool to focus on the specific language used in the application, the tool can more accurately identify relevant issues and reduce the number of false positives. Additionally, tuning the rule set ensures that the tool's checks are appropriate for the application's context, further improving the accuracy of the scan results.
Reference: CompTIA SecurityX Study Guide: Discusses best practices for configuring code scanning tools, including language-specific tuning and rule set adjustments.
"Secure Coding: Principles and Practices" by Mark
G. Graff and Kenneth R. van Wyk: Highlights the importance of customizing code analysis tools to reduce false positives.
OWASP (Open Web Application Security Project): Provides guidelines for configuring and tuning code scanning tools to improve accuracy.
정답:
Explanation:
A centralized Software Bill of Materials (SBoM) is the best solution for identifying vulnerabilities in container images in aprivate repository. An SBoM provides a comprehensive inventory of all components, dependencies, and their versions within a container image, facilitating quick evaluation and response to vulnerabilities.
Why Centralized SBoM?
Comprehensive Inventory: An SBoM lists all software components, including their versions and dependencies, allowing for thorough vulnerability assessments.
Quick Identification: Centralizing SBoM data enables rapid identification of affected containers when a vulnerability is disclosed.
Automation: SBoMs can be integrated into automated tools for continuous monitoring and alerting of vulnerabilities.
Regulatory Compliance: Helps in meeting compliance requirements by providing a clear and auditable record of all software components used.
Other options, while useful, do not provide the same level of comprehensive and efficient vulnerability management:
A. SAST scan reports: Focuses on static analysis of code but may not cover all components in container images.
C. CIS benchmark compliance reports: Ensures compliance with security benchmarks but does not provide detailed component inventory.
D. Credentialed vulnerability scan: Useful for in-depth scans but may not be as efficient for quick
vulnerability evaluation.
Reference: CompTIA SecurityX Study Guide
"Software Bill of Materials (SBoM)," NIST Documentation "Managing Container Security with SBoM," OWASP
정답:
Explanation:
To ensure always-on VPN access is enabled and restricted to company assets, the network engineer needs to generate device certificates using the specific template settings required for the company's VPN solution. These certificates ensure that only authorized devices can establish a VPN connection.
Why Device Certificates are Necessary:
Authentication: Device certificates authenticate company assets, ensuring that only authorized devices can access the VPN.
Security: Certificates provide a higher level of security compared to username and password combinations, reducing the risk of unauthorized access.
Compliance: Certificates help in meeting security policies and compliance requirements by ensuring that only managed devices can connect to the corporate network.
Other options do not provide the same level of control and security for always-on VPN access: B. Modify signing certificates for IKE version 2: While important for VPN protocols, it does not address device-specific authentication.
C. Create a wildcard certificate: This is not suitable for device-specific authentication and could introduce security risks.
D. Add the VPN hostname as a SAN entry: This is more related to certificate management and does
not ensure device-specific authentication.
Reference: CompTIA SecurityX Study Guide
"Device Certificates for VPN Access," Cisco Documentation NIST Special Publication 800-77, "Guide to IPsec VPNs"