Question No : 1
An event from which IBM Security Verify report is represented by the image below?
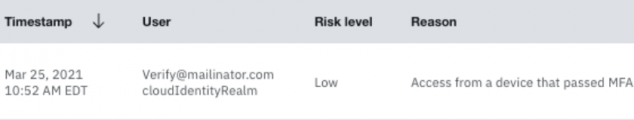
정답:
Question No : 2
How does an access policy for SSO enhance application security?
정답:
Question No : 3
Why is it important to apply access policies to the admin console?
정답:
Question No : 4
What is the primary benefit of adding a federated identity source to a user management system?
정답:
Question No : 5
What type of analysis would be most useful to identify patterns of unusual activity in system access logs?
정답:
Question No : 6
Why are recertification campaigns important in user access governance?
정답:
Question No : 7
What is the importance of assigning specific privacy rules to a policy? (Choose Two)
정답:
Question No : 8
What is the primary purpose of SSL certificates in web administration?
정답:
Question No : 9
Which of the following features should a well-integrated Developer Portal in Verify offer? (Choose Two)
정답:
Question No : 10
When adding a new attribute to a user profile, which considerations should be made? (Choose Two)
정답:
Question No : 11
Why would an application use JWT tokens for authentication? (Choose Two)
정답:
Question No : 12
What are two types of application access policies that can be authored in IBM Security Verify?
정답:
Question No : 13
Which statement is true in regards to federated users, users created in an Identity source realm?
정답:
Question No : 14
What are common types of applications integrated with SSO solutions? (Choose Two)
정답:
Question No : 15
What differentiates a native application from a federated application in SSO contexts? (Choose Three)
정답:
