Certified Cybersecurity Technician(C|CT) 온라인 연습
최종 업데이트 시간: 2025년10월10일
당신은 온라인 연습 문제를 통해 EC-Council 212-82 시험지식에 대해 자신이 어떻게 알고 있는지 파악한 후 시험 참가 신청 여부를 결정할 수 있다.
시험을 100% 합격하고 시험 준비 시간을 35% 절약하기를 바라며 212-82 덤프 (최신 실제 시험 문제)를 사용 선택하여 현재 최신 60개의 시험 문제와 답을 포함하십시오.
정답:
Explanation:
Obfuscating is the technique used by Kevin to evade the IDS system in the above scenario. Obfuscating is a technique that involves encoding or modifying packets or data with various methods or characters to make them unreadable or unrecognizable by an IDS (Intrusion Detection System). Obfuscating can be used to bypass or evade an IDS system that relies on signatures or patterns to detect malicious activities. Obfuscating can include encoding packets with Unicode characters, which are characters that can represent various languages and symbols. The IDS system cannot recognize the packet, but the target web server can decode them and execute them normally. Desynchronization is a technique that involves creating discrepancies or inconsistencies between the state of a connection as seen by an IDS system and the state of a connection as seen by the end hosts. Desynchronization can be used to bypass or evade an IDS system that relies on stateful inspection to track and analyze connections. Desynchronization can include sending packets with invalid sequence numbers, which are numbers that indicate the order of packets in a connection. Session splicing is a technique that involves splitting or dividing packets or data into smaller fragments or segments to make them harder to detect by an IDS system. Session splicing can be used to bypass or evade an IDS system that relies on packet size or content to detect malicious activities. Session splicing can include sending packets with small MTU (Maximum Transmission Unit) values, which are values that indicate the maximum size of packets that can be transmitted over a network. An urgency flag is a flag in the TCP (Transmission Control Protocol) header that indicates that the data in the packet is urgent and should be processed immediately by the receiver. An urgency flag is not a technique to evade an IDS system, but it can be used to trigger an IDS system to generate an alert or a response.
정답:
Explanation:
128 is the TTL value that Henry obtained, which indicates that the target OS is Windows. TTL (Time to Live) is a field in the IP (Internet Protocol) header that specifies how long a packet can remain in a network before it is discarded or dropped. TTL is usually expressed in seconds or hops (the number of routers or gateways that a packet passes through). TTL is used to prevent packets from looping endlessly in a network or consuming network resources. Different operating systems have different default TTL values for their packets. By observing the TTL value of a packet from a target system or network, one can infer the operating system of the target.
Some common TTL values and their corresponding operating systems are:
64: Linux, Unix, Android
128: Windows
255: Cisco IOS
60: Mac OS
In the scenario, Henry used Nmap tool to discover the OS of the target system. Nmap (Network Mapper) is a tool that can perform various network scanning and enumeration tasks, such as port scanning, OS detection, service identification, etc. Nmap can use various techniques to detect the OS of a target system, such as TCP/IP fingerprinting, which involves analyzing various TCP/IP characteristics of packets from the target system, such as TTL value. In the scenario, Henry obtained a TTL value of 128 , which indicates that the target OS is Windows.
정답:
Explanation:
HIPPA/PHI is the regulation that is mostly violated in the above scenario. HIPPA (Health Insurance Portability and Accountability Act) is a US federal law that sets standards for protecting the privacy and security of health information. PHI (Protected Health Information) is any information that relates to the health or health care of an individual and that can identify the individual, such as name, address, medical records, etc. HIPPA/PHI requires covered entities, such as health care providers, health plans, or health care clearinghouses, and their business associates, to safeguard PHI from unauthorized access, use, or disclosure. In the scenario, the medical company experienced a major cyber security breach that exposed the personal medical records of many patients on the internet, which violates HIPPA/PHI regulations. PII (Personally Identifiable Information) is any information that can be used to identify a specific individual, such as name, address, social security number, etc. PII is not specific to health information and can be regulated by various laws, such as GDPR (General Data Protection Regulation), CCPA (California Consumer Privacy Act), etc. PCI DSS (Payment Card Industry Data Security Standard) is a set of standards that applies to entities that store, process, or transmit payment card information, such as merchants, service providers, or payment processors. PCI DSS requires them to protect cardholder data from unauthorized access, use, or disclosure. ISO 2002 (International Organization for Standardization 2002) is not a regulation, but a standard for information security management systems that provides guidelines and best practices for organizations to manage their information security risks.
정답:
Explanation:
Weaponization is the stage of the cyber kill chain that you are at in the above scenario. The cyber kill chain is a model that describes the phases of a cyberattack from the perspective of the attacker. The cyber kill chain consists of seven stages: reconnaissance, weaponization, delivery, exploitation, installation, command and control, and actions on objectives. Reconnaissance is the stage of the cyber kill chain that involves gathering information about the target, such as IP addresses, domain names, vulnerabilities, etc. Weaponization is the stage of the cyber kill chain that involves creating a malicious payload or tool that can exploit the target’s vulnerabilities. Weaponization can include creating a client-side backdoor to send it to the employees via email. Delivery is the stage of the cyber kill chain that involves transmitting or delivering the weaponized payload or tool to the target’s system or network. Exploitation is the stage of the cyber kill chain that involves executing or triggering the weaponized payload or tool on the target’s system or network.
정답:
Explanation:
Quid pro quo is the social engineering technique that Johnson employed in the above scenario. Quid pro quo is a social engineering method that involves offering a service or a benefit in exchange for information or access. Quid pro quo can be used to trick victims into believing that they are receiving help or assistance from a legitimate source, while in fact they are compromising their security or privacy. In the scenario, Johnson performed quid pro quo by claiming himself to represent a technical support team from a vendor and offering to help sibertech.org with a server issue, while in fact he prompted the victim to execute unusual commands and install malicious files, which were then used to collect and pass critical information to Johnson’s machine. If you want to learn more about social engineering techniques, you can check out these resources:
[1] A guide to different types of social engineering attacks and how to prevent them: [https://www.csoonline.com/article/2124681/what-is-social-engineering.html]
[2] A video that explains how quid pro quo works and how to avoid falling for it: [https://www.youtube.com/watch?v=3Yy0gZ9xw8g]
[3] A quiz that tests your knowledge of social engineering techniques and scenarios: [https://www.proprofs.com/quiz-school/story.php?title=social-engineering-quiz]
정답:
Explanation:
Quid pro quo is the social engineering technique that Johnson employed in the above scenario. Social engineering is a technique that involves manipulating or deceiving people into performing actions or revealing information that can be used for malicious purposes. Social engineering can be performed through various methods, such as phone calls, emails, websites, etc. Quid pro quo is a social engineering method that involves offering a service or a benefit in exchange for information or access. Quid pro quo can be used to trick victims into believing that they are receiving help or assistance from a legitimate source, while in fact they are compromising their security or privacy. In the scenario, Johnson performed quid pro quo by claiming himself to represent a technical support team from a vendor and offering to help sibertech.org with a server issue, while in fact he prompted the victim to execute unusual commands and install malicious files, which were then used to collect and pass critical information to Johnson’s machine. Diversion theft is a social engineering method that involves diverting the delivery or shipment of goods or assets to a different location or destination. Elicitation is a social engineering method that involves extracting information from a target by engaging them in a conversation or an interaction. Phishing is a social engineering method that involves sending fraudulent emails or messages that appear to come from a trusted source, such as a bank, a company, or a person, and asking the recipient to click on a link, open an attachment, or provide personal or financial information.
정답:
Explanation:
Yes is the answer to whether the file has been modified or not in the above scenario. A hash is a fixed-length string that is generated by applying a mathematical function, called a hash function, to a piece of data, such as a file or a message. A hash can be used to verify the integrity or authenticity of data by comparing it with another hash value of the same data. A hash value is unique and any change in the data will result in a different hash value. To compare the hash value of the original file with the leaked file and state whether the file has been modified or not, one has to follow these steps:
Navigate to Hash folder in Documents of Attacker-1 machine.
Open OriginalFileHash.txt file with a text editor.
Note down the MD5 hash value of the original file as 8f14e45fceea167a5a36dedd4bea2543 Open Command Prompt and change directory to Hash folder using cd command.
Type certutil -hashfile Sensitiveinfo.txt MD5 and press Enter key to generate MD5 hash value of leaked file.
Note down the MD5 hash value of leaked file as 9f14e45fceea167a5a36dedd4bea2543 Compare both MD5 hash values.
The MD5 hash values are different, which means that the file has been modified.
정답:
Explanation:
Temp_High is the command that was sent by the IoT device over the network in the above scenario. An IoT (Internet of Things) device is a device that can connect to the internet and communicate with other devices or systems over a network. An IoT device can send or receive commands or data for various purposes, such as monitoring, controlling, or automating processes. To analyze the IoT device traffic file and determine the command that was sent by the IoT device over the network, one has to follow these steps:
Navigate to the Documents folder of Attacker-1 machine.
Double-click on loTdeviceTraffic.pcapng file to open it with Wireshark.
Click on Analyze menu and select Display Filters option.
Enter udp.port == 5000 as filter expression and click on Apply button.
Observe the packets filtered by the expression.
Click on packet number 4 and expand User Datagram Protocol section in packet details pane.
Observe the data field under User Datagram Protocol section.
The data field under User Datagram Protocol section is 54:65:6d:70:5f:48:69:67:68 , which is hexadecimal representation of Temp_High , which is the command that was sent by the IoT device over the network.
정답:
Explanation:
정답:
Explanation:
FTP Unencrypted Cleartext Login is the vulnerability that may affect the website according to the severity factor in the above scenario. A vulnerability is a weakness or flaw in a system or network that can be exploited by an attacker to compromise its security or functionality. A vulnerability assessment is a process that involves identifying, analyzing, and evaluating vulnerabilities in a system or network using various tools and techniques. Greenbone is a tool that can perform vulnerability assessment on various targets using various tests and scans. To perform a vulnerability assessment on the given IP address 20.20.10.26, one has to follow these steps: Open a web browser and type 20.20.10.26:9392
Press Enter key to access the Greenbone web interface.
Enter admin as username and password as password.
Click on Login button.
Click on Scans menu and select Tasks option.
Click on Start Scan icon next to IP Address Scan task.
Wait for the scan to complete and click on Report icon next to IP Address Scan task.
Observe the vulnerabilities found by the scan.
The vulnerabilities found by the scan are:
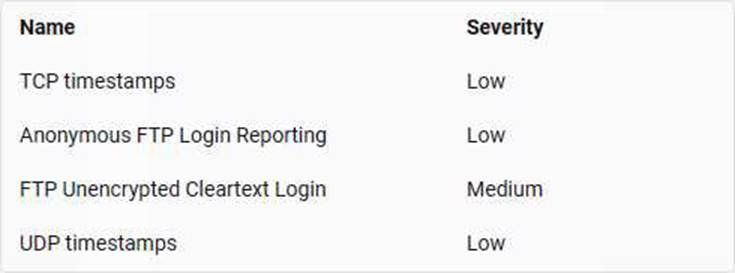
The vulnerability that may affect the website according to the severity factor is FTP Unencrypted Cleartext Login, which has a medium severity level. FTP Unencrypted Cleartext Login is a vulnerability that allows an attacker to intercept or sniff FTP login credentials that are sent in cleartext over an unencrypted connection. An attacker can use these credentials to access or modify files or data on the FTP server. TCP timestamps and UDP timestamps are vulnerabilities that allow an attacker to estimate the uptime of a system or network by analyzing the timestamp values in TCP or UDP packets. Anonymous FTP Login Reporting is a vulnerability that allows an attacker to access an FTP server anonymously without providing any username or password.
정답:
Explanation:
TCP/UDP is the protocol that has been used to apply the rule to block the web application www.abchacker.com in the above scenario. pfSense is a firewall and router software that can be installed on a computer or a device to protect a network from various threats and attacks. pfSense can be configured to block or allow traffic based on various criteria, such as source, destination, port, protocol, etc. pfSense rules are applied to traffic in the order they appear in the firewall configuration. To perform an analysis on the rules set by the admin, one has to follow these steps:
Open a web browser and type 20.20.10.26
Press Enter key to access the pfSense web interface.
Enter admin as username and admin@l23 as password.
Click on Login button.
Click on Firewall menu and select Rules option.
Click on LAN tab and observe the rules applied to LAN interface.
The rules applied to LAN interface are:
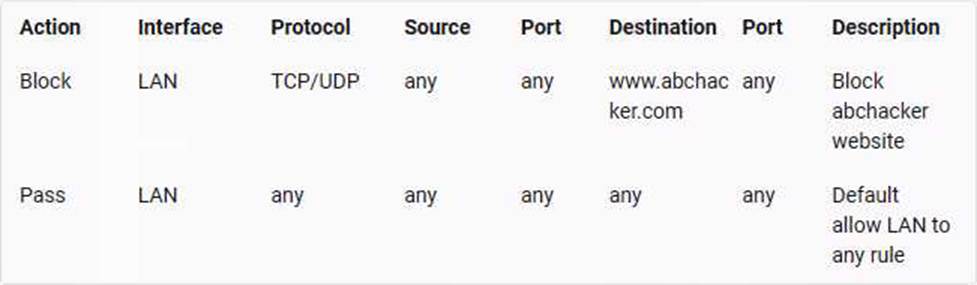
The first rule blocks any traffic from LAN interface to www.abchacker.com website using TCP/UDP protocol. The second rule allows any traffic from LAN interface to any destination using any protocol. Since the first rule appears before the second rule, it has higher priority and will be applied first. Therefore, TCP/UDP is the protocol that has been used to apply the rule to block the web application www.abchacker.com. POP3 (Post Office Protocol 3) is a protocol that allows downloading emails from a mail server to a client device. FTP (File Transfer Protocol) is a protocol that allows transferring files between a client and a server over a network. ARP (Address Resolution Protocol) is a protocol that resolves IP addresses to MAC (Media Access Control) addresses on a network.
정답:
Explanation:
4 is the UID that is mapped to user john in the database table in the above scenario. SQL injection is a type of web application attack that exploits a vulnerability in a web application that allows an attacker to inject malicious SQL statements into an input field, such as a username or password field, and execute them on the database server. SQL injection can be used to bypass authentication, access or modify sensitive data, execute commands, etc. To exploit the web application and fetch the user credentials, one has to follow these steps:
Open a web browser and type www.movieabc.com
Press Enter key to access the web application.
Enter sam as username and test as password.
Click on Login button.
Observe that a welcome message with username sam is displayed.
Click on Logout button.
Enter sam’ or ‘1’='1 as username and test as password.
Click on Login button.
Observe that a welcome message with username admin is displayed, indicating that SQL injection was successful.
Click on Logout button.
Enter sam’; SELECT * FROM users; C as username and test as password.
Click on Login button.
Observe that an error message with user credentials from users table is displayed.
The user credentials from users table are:
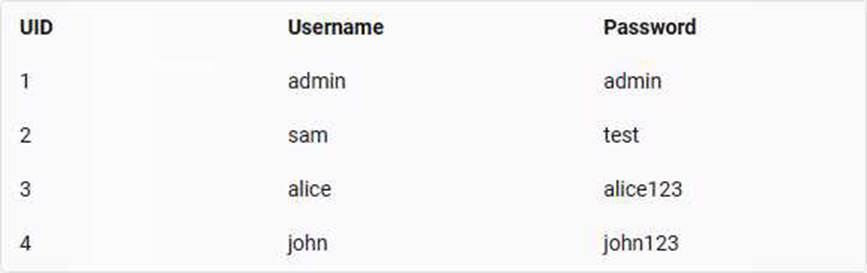
The UID that is mapped to user john is 4.
정답:
Explanation:
정답:
Explanation:
hat@red is the FTP credential that was stolen using Cain and Abel in the above scenario. FTP (File Transfer Protocol) is a protocol that allows transferring files between a client and a server over a network. FTP requires a username and a password to authenticate the client and grant access to the server. Cain and Abel is a tool that can perform various network attacks, such as ARP poisoning, password cracking, sniffing, etc. Cain and Abel can poison the machine and fetch the FTP credentials used by the admin by intercepting and analyzing the network traffic. To validate the credentials that were stolen using Cain and Abel and read the file flag.txt, one has to follow these steps: Navigate to the Documents folder of Attacker-1 machine.
Double-click on Cain.exe file to launch Cain and Abel tool.
Click on Sniffer tab.
Click on Start/Stop Sniffer icon.
Click on Configure icon.
Select the network adapter and click on OK button.
Click on + icon to add hosts to scan.
Select All hosts in my subnet option and click on OK button.
Wait for the hosts to appear in the list.
Right-click on 20.20.10.26 (FTP server) and select Resolve Host Name option.
Note down the host name as ftpserver.movieabc.com
Click on Passwords tab.
Click on + icon to add items to list.
Select Network Passwords option.
Select FTP option from Protocol drop-down list.
Click on OK button.
Wait for the FTP credentials to appear in the list.
Note down the username as hat and the password as red
Open a web browser and type ftp://hat:[email protected]
Press Enter key to access the FTP server using the stolen credentials.
Navigate to flag.txt file and open it.
Read the file content.
정답:
Explanation:
3 is the number of files present in the folder in the above scenario. A RAT (Remote Access Trojan) is a type of malware that allows an attacker to remotely access and control a compromised system or network. A RAT can be used to steal sensitive data, spy on user activity, execute commands, install other malware, etc. To initiate a remote connection using thief client, one has to follow these steps: Navigate to the thief folder located at Z:\CCT-Tools\CCT Module 01 Information Security Threats and Vulnerabilities\Remote Access Trojans (RAT)\Thief of Attacker Machine-1. Double-click on thief.exe file to launch thief client.
Enter 20.20.10.26 as IP address of server.
Enter 1234 as port number.
Click on Connect button.
After establishing connection with server, click on Browse button.
Navigate to Desktop folder on server.
Count number of files present in folder.
The number of files present in folder is 3, which are:
Sensitive corporate docs.docx
Sensitive corporate docs.pdf
Sensitive corporate docs.txt