Check Point Certified Security Administrator R81.20 온라인 연습
최종 업데이트 시간: 2025년10월10일
당신은 온라인 연습 문제를 통해 Check Point 156-215.81.20 시험지식에 대해 자신이 어떻게 알고 있는지 파악한 후 시험 참가 신청 여부를 결정할 수 있다.
시험을 100% 합격하고 시험 준비 시간을 35% 절약하기를 바라며 156-215.81.20 덤프 (최신 실제 시험 문제)를 사용 선택하여 현재 최신 369개의 시험 문제와 답을 포함하십시오.
정답:
Explanation:
ThreatWiki is a web-based tool that provides statistics on detected threats, such as attack types, sources, destinations, and severity. It also allows the administrator to search for specific threats and view their details and mitigation methods. The other options are not tools for viewing statistics on detected threats.
Reference: [ThreatWiki], [ThreatWiki - Threat Emulation]
정답:
Explanation:
A shared policy is a set of rules that can be used in multiple policy packages. It allows the administrator to create a common security policy for different gateways or domains, and avoid duplication and inconsistency. The other options are not advantages of a shared policy.
Reference: [Shared Policies Overview], [Shared Policies Best Practices]
정답:
Explanation:
SmartLog is a unified log viewer that provides fast and easy access to logs from all Check Point components3. It allows the administrator to query for any log field, such as the IP address of the tablet, and filter the results by time, severity, blade, action, and more4. SmartView Tracker is a legacy tool that displays network activity logs from Security Gateways and other Check Point devices. It does not support remote connection to the wireless controller or querying for specific IP addresses.
Reference: SmartLog, SmartLog Queries, [SmartView Tracker]
정답:
Explanation:
The Check Point Upgrade Service Engine (CPUSE) is a tool that automates the process of upgrading and installing Check Point products on Gaia OS1. It can also be used to update the Gaia OS itself2. The other options are not valid tools for this purpose.
Reference: Check Point Upgrade Service Engine (CPUSE) - Gaia Deployment Agent, Check Point R81 Gaia Installation and Upgrade Guide
정답:
Explanation:
The commands you could use to set the IP to 192.168.80.200/24 and default gateway to 192.168.80.1 after the initial installation on Check Point appliance are:
set interface Mgmt ipv4-address 192.168.80.200 mask-length 24. This command sets the IPv4 address and subnet mask of the Management interface.
set static-route default nexthop gateway address 192.168.80.1 on. This command sets the default gateway for IPv4 routing.
save config. This command saves the configuration changes.
Reference: [Check Point R81 Gaia CLI Reference Guide], [Check Point R81 Gaia Administration Guide]
정답:
Explanation:
To achieve the requirement of giving the Network Operations Center administrator access to Check Point Security devices mostly for troubleshooting purposes, but not to the expert mode, and still allowing her to run tcpdump, you need to:
Add tcpdump to CLISH using add command. This command adds a new command to the Command Line Interface Shell (CLISH) that allows running tcpdump without entering the expert mode. Create a new access role. This option defines a set of permissions and commands that can be assigned to a user or a group of users.
Add tcpdump to the role. This option grants the permission to run tcpdump to the role.
Create new user with any UID and assign role to the user. This option creates a new user account with any User ID (UID) and assigns the role that has tcpdump permission to the user.
Reference: [How to add a new command to CLISH], [Check Point R81 Gaia Administration Guide], [Check Point R81 Identity Awareness Administration Guide]
정답:
Explanation:
The purpose of the CPCA process is generating and modifying certificates. CPCA stands for Check Point Certificate Authority and it is a process that runs on the Security Management Server or Log Server. It is responsible for creating and managing certificates for internal communication between Check Point components, such as SIC.
Reference: [Check Point R81 Quantum Security Management Administration Guide], [Check Point R81 Quantum Security Gateway Guide]
정답:
Explanation:
The ports to which the Client Authentication daemon listens on by default are 259 and 900. Client Authentication is a method that allows users to authenticate with the Security Gateway before they are allowed access to protected resources. The Client Authentication daemon (fwauthd) runs on the Security Gateway and listens for authentication requests on TCP ports 259 and 900.
Reference: [Check Point R81 Remote Access VPN Administration Guide], [Check Point R81 Quantum Security Gateway Guide]
정답:
Explanation:
The communication between different Check Point components is secured in R80 by using SIC. SIC stands for Secure Internal Communication and it is a mechanism that ensures the authenticity and confidentiality of communication between Check Point components, such as Security Gateways, Security Management Servers, Log Servers, etc. SIC uses certificates issued by the Internal CA (ICA) and encryption algorithms such as AES-25634.
Reference: Check Point R81 Quantum Security
Gateway Guide, Check Point R81 Quantum Security Management Administration Guide
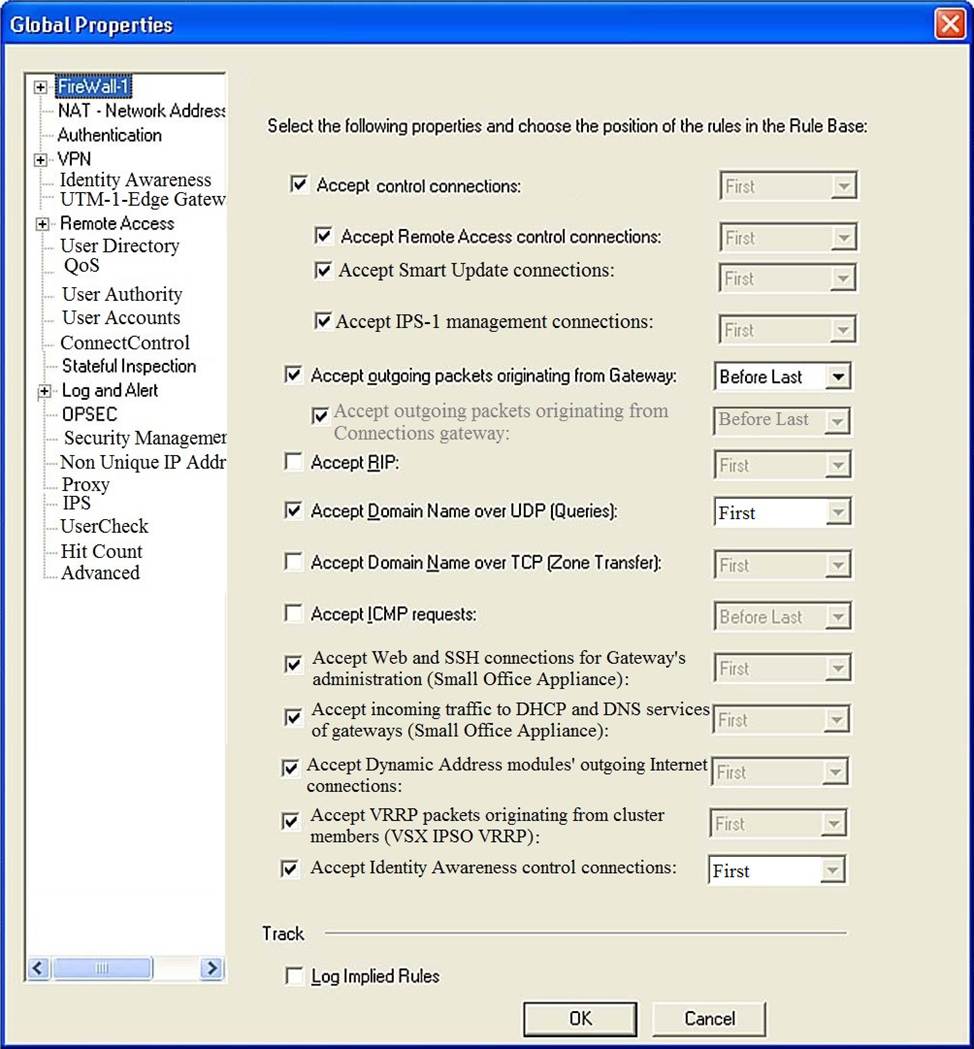
정답:
Explanation:
The selected option “Accept Domain Name over UDP (Queries)” means that UDP Queries will be accepted by the traffic allowed only through interfaces with external anti-spoofing topology and this will be done before first explicit rule written by Administrator in a Security Policy. This option enables the Security Gateway to accept DNS queries from external hosts and forward them to internal DNS servers. The queries are accepted by an implied rule that is applied before the explicit rules in the Security Policy. The implied rule only allows queries from interfaces that have external anti-spoofing groups defined.
Reference: Check Point R81 Quantum Security Gateway Guide, Implied Rules
정답:
Explanation:
The destination server for Security Gateway logs depends on a Security Management Server configuration. This is true because the Security Management Server defines the log servers that receive logs from the Security Gateways. The log servers can be either the Security Management Server itself or a dedicated Log Server12.
Reference: Check Point R81 Logging and Monitoring
Administration Guide, Check Point R81 Quantum Security Gateway Guide
정답: C
Explanation:
The steps you will need to do in SmartConsole in order to get the connection working behind the Internet Security Gateway are:
Define an accept rule in Security Policy. This rule allows the traffic from your internal networks to pass through the Security Gateway.
Define automatic NAT for each network to NAT the networks behind a public IP. This option translates the private IP addresses of your internal networks to a public IP address assigned by your ISP router. This way, your internal networks can communicate with the Internet using a valid IP address. Publish and install the policy. This step applies the changes you made to the Security Gateway and activates the security and NAT rules.
Reference: Check Point R81 Quantum Security Gateway Guide
정답:
Explanation:
The Check Point software blade that monitors Check Point devices and provides a picture of network and security performance is Monitoring. The Monitoring Software Blade presents a complete picture of network and security performance, enabling fast responses to changes in traffic patterns or security events. It centrally monitors Check Point devices and alerts security administrators to changes to gateways, endpoints, tunnels, remote users and security activities234.
Reference: Monitoring Software Blade, Check Point Integrated Security Architecture, Support, Support Requests, Training, Documentation, and Knowledge base for Check Point products and services
정답:
Explanation:
The changes made by an administrator before publishing the session can be seen by a superuser administrator from Manage and Settings > Sessions, right click on the session and click ‘View Changes…’. This option allows the superuser to review the changes made by another administrator in a pending session1.
Reference: Check Point R81 Security Management Administration Guide
정답:
Explanation:
The position of an implied rule is manipulated in the Global Properties window. Implied rules are predefined rules that are not displayed in the rule base. They allow or block traffic for essential services such as communication with Check Point servers, logging, and VPN traffic. The position of an implied rule can be changed in the Global Properties > Firewall > Implied Rules section56.
Reference: How to view Implied Rules in R80.x / R81.x SmartConsole, Implied Rules