Forescout Certified Professional 온라인 연습
최종 업데이트 시간: 2025년11월06일
당신은 온라인 연습 문제를 통해 Forescout FSCP 시험지식에 대해 자신이 어떻게 알고 있는지 파악한 후 시험 참가 신청 여부를 결정할 수 있다.
시험을 100% 합격하고 시험 준비 시간을 35% 절약하기를 바라며 FSCP 덤프 (최신 실제 시험 문제)를 사용 선택하여 현재 최신 80개의 시험 문제와 답을 포함하십시오.
정답:
Explanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Blog on Post-Connect Access Controls and the Comply-to-Connect framework documentation, a Post-Connect Methodology is best defined as treating endpoints as "Innocent until proven guilty".
Definition of Post-Connect Methodology:
According to the official documentation:
"Post-connect" is described as treating endpoints as innocent until they are proven guilty. They can connect to the network, during and after which they are assessed for acceptance criteria."
How Post-Connect Works:
According to the Post-Connect Access Controls blog:
Initial Connection - Endpoints are allowed to connect to the network immediately (innocent)
Assessment During/After Connection - After connecting, endpoints are assessed for acceptance criteria
Compliance Checking - Endpoints are checked for:
Corporate asset status (must be company-owned)
Security compliance (antivirus, patches, encryption, etc.)
Remediation or Quarantine - Based on assessment results: Compliant endpoints: Full access Non-compliant endpoints: Placed in quarantine for remediation Post-Connect vs. Pre-Connect:
According to the Comply-to-Connect documentation:
Pre-Connect - "Guilty until proven innocent" - Endpoint must prove compliance BEFORE getting network access
Post-Connect - "Innocent until proven guilty" - Endpoint connects first, then compliance is assessed
Benefits of Post-Connect Methodology:
According to the documentation:
"The greatest benefit to the post-connect approach is a positive user experience. Unless a system is out of compliance and ends up in a quarantine, your company's users have no idea access controls are even taking place on the network."
Acceptance Criteria in Post-Connect:
According to the framework:
Corporate Asset Verification - Determines if the endpoint belongs to the organization
Compliance Assessment - Checks for:
Updated antivirus
Patch levels
Disk encryption status
Security tool functionality
If an endpoint fails these criteria, it's placed in quarantine (controlled network access) rather than being completely blocked.
Why Other Options Are Incorrect:
A. 802.1X is a flavor of Post-Connect - 802.1X is a pre-connect access control method (requires authentication before network access)
B. Guilty until proven innocent - This describes pre-connect methodology, not post-connect
D. Used subsequent to pre-connect - While post-connect can follow pre-connect, this doesn't define what post-connect is
E. Assessed for critical compliance before IP address is assigned - This describes pre-connect methodology
Referenced Documentation:
Forescout Blog - Post-Connect Access Controls Comply-to-Connect Brief - Pre-connect vs Post-connect comparison Achieving Comply-to-Connect Requirements with Forescout
정답:
Explanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout User Directory Plugin Configuration Guide and YouTube tutorial for User Directory integration, the Server Name field is NOT editable once the User Directory server is configured. Once a server configuration is saved, the Server Name cannot be changed; it can only be modified by deleting and reconfiguring the server entry.
User Directory Server Configuration Fields:
According to the User Directory plugin configuration documentation:
When initially adding a server, these fields are configured:
Server Name - Identifier for the server (e.g., "lab", "production-ad")
Address - IP address or FQDN (e.g., 192.168.1.100)
Port - Connection port (e.g., 389, 636)
Domain - Domain name (e.g., example.com)
Administrator - Account credentials for authentication
Password - Password for the administrator account
Editable Fields After Configuration:
According to the configuration workflow:
After the User Directory server is initially configured, the following fields CAN be edited:
Administrator - Can be changed to update authentication credentials
Password - Can be updated if credentials change
Port - Can be modified if the connection port changes
Address - Can be changed to point to a different server
Domain - Can be updated if domain name changes
Non-Editable Field:
According to the User Directory plugin behavior:
The Server Name is used as the primary identifier for the User Directory server configuration in
Forescout. Once created, this identifier cannot be modified because it:
Serves as the unique identifier in the Forescout database Is referenced by other configurations and policies Changing it would break existing policy references Must be deleted and recreated to change Verification Workflow:
According to the tutorial documentation:
After creating a User Directory server configuration with:
Server Name: "lab"
Address: 192.168.1.50
Port: 389
Domain: example.com
Administrator: domain\admin
Password: [configured]
Once saved and applied, the Server Name "lab" cannot be edited. To change it, you would need to delete the entire configuration and create a new one with a different name.
Why Other Fields Are Editable:
A. Administrator - ✓ Editable; credentials may need to be updated
C. Password - ✓ Editable; security practice requires periodic password changes D. Address - ✓ Editable; server may move to a different IP
E. Port - ✓ Editable; port configuration may change based on security requirements
Referenced Documentation:
Forescout User Directory Plugin - Integration tutorial
Configure server settings documentation
User Directory Plugin Configuration - Initial Setup documentation
정답:
Explanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Installation Guide and Windows Vulnerability DB Configuration Guide, a characteristic of a centralized deployment is that checking Microsoft vulnerabilities at a remote site may have significant bandwidth impact.
Centralized vs. Distributed Deployment Models:
In a centralized deployment, Forescout uses a central location with Enterprise Manager and Appliances, while in a distributed deployment, appliances are placed at multiple locations.
Bandwidth Considerations in Centralized Deployments:
According to the Windows Vulnerability DB Configuration Guide:
"Minimize Bandwidth During Vulnerability File Download: You can minimize bandwidth usage during Microsoft vulnerability file download processes by limiting the number of concurrent HTTP downloads to endpoints. The default is 20 endpoints simultaneously."
The documentation further states:
"To customize: Select Tools>Options>HPS Inspection Engine>Windows Updates tab. Define a value in
the Maximum Concurrent Vulnerability DB File HTTP Uploads field."
This configuration option exists specifically because checking Microsoft vulnerabilities (downloading vulnerability definition files to endpoints and having endpoints upload compliance data back) can consume significant bandwidth.
Why Centralized Deployments Magnify Bandwidth Impact:
According to the Installation Guide:
In a centralized deployment:
All vulnerability checking traffic flows through a single central location
Multiple endpoints simultaneously download large vulnerability database files
All endpoints upload vulnerability compliance data back to central appliances
All this traffic concentrates at the central site
In contrast, in a distributed deployment where appliances exist at remote sites, local endpoints can communicate directly with the local appliance without impacting the central WAN link.
Bandwidth Management for Centralized Deployments:
According to the documentation:
To address the bandwidth impact in centralized deployments:
Limit concurrent HTTP uploads for vulnerability DB files
Schedule vulnerability checks during off-peak hours
Carefully plan deployment architecture considering remote site bandwidth
Why Other Options Are Incorrect:
B. Provides enhanced IPS and HTTP actions - This is not specific to centralized deployments; both deployment models can use IPS and HTTP actions
C. Is optimal for threat protection - Neither deployment model is necessarily optimal; choice depends on specific requirements
D. Deployed as a Layer-2 channel - Deployment mode (Layer-2 vs. Layer-3) is independent of centralized vs. distributed architecture
E. Every site has an appliance - This describes a distributed deployment, not a centralized one. In centralized deployments, appliances are concentrated at a central site
Centralized Deployment Characteristics:
According to the documentation:
Appliances are typically located at a central site
Remote sites connect through WAN links
Reduced operational complexity with centralized management
Higher bandwidth requirements on WAN for vulnerability checking and policy enforcement
Requires careful bandwidth planning for remote vulnerability assessment
Referenced Documentation:
Forescout Platform Installation Guide - Network Deployment Requirements
Windows Vulnerability DB Configuration Guide - Minimize Bandwidth During Vulnerability File Download
Forescout Platform Cloud Strategies and Best Practices - Bandwidth considerations
정답:
Explanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout User Directory Plugin Configuration Guide and supported integration documentation, Replica is NOT available when initially adding a server to the User Directory Plugin. Replicas are configured after the initial server setup is complete.
User Directory Server Initial Setup Process:
When initially adding a User Directory server, the following settings are available:
Server Name - The name to identify the server in Forescout Address - The IP address or FQDN of the User Directory server Port - The port number (typically 389 for LDAP, 636 for secure LDAP) Domain - The domain name associated with the User Directory Test - Option to test the connection and credentials
Advanced - Advanced configuration options
Replica Configuration - Post-Initial Setup:
According to the documentation:
"After configuring server settings, you can configure server tests and replicas."
The Replica settings are NOT available during the initial server addition. Instead, replicas are configured as a separate step after the primary server configuration is complete.
Replica Setup Workflow:
According to the User Directory Plugin configuration process:
Step 1: Add Server - Configure the primary server with Name, Address, Port, Domain
Step 2: Test Connection - Use the Test option to verify connectivity
Step 3: Configure Replicas - After the primary server is fully configured, then add replica servers
The documentation explicitly states:
"Refer to the following sections for server configuration details. After configuring server settings, you can configure server tests and replicas."
Why Other Options Are Available Initially:
A. Test - ✓ Available initially; allows testing of server credentials and connectivity before completion B. Domain - ✓ Available initially; domain name is required during server setup
C. Domain Aliases - ✓ Available initially; additional domain aliases can be specified for the server
D. Advanced - ✓ Available initially; advanced options like authentication types, TLS, etc. are available during setup
Replica Purpose:
Replicas are used to provide redundancy and failover capability. According to the documentation:
When replica servers are configured:
If the primary User Directory server becomes unavailable, the Forescout platform can failover to a replica server
Multiple replicas can be specified for increased fault tolerance
Referenced Documentation:
Forescout User Directory Plugin Configuration - Server Setup documentation
Configure server settings - After configuring server settings section
User Directory Plugin configuration videos and tutorials showing initial setup flow
정답: 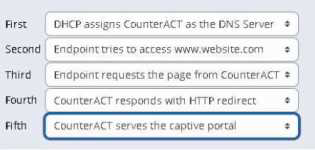
정답:
Explanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Resiliency Solutions User Guide and the Forescout Platform Installation Guide, High Availability (HA) requires a license. The documentation explicitly states:
"If your deployment is using Centralized Licensing Mode, you must acquire a valid ForeScout CounterACT Resiliency license. The Resiliency license supports: High Availability Pairing for Enterprise Manager is supported by the Forescout CounterACT See License."
High Availability Licensing Requirements:
According to the official documentation:
Per-Appliance Licensing Mode:
"The demo license for your High Availability system is valid for 30 days. You must install a permanent license before this period expires."
Centralized Licensing Mode:
"If your deployment is using Centralized Licensing Mode, you must acquire a valid ForeScout CounterACT Resiliency license for Appliances, or a CounterACT See License for Enterprise Manager High Availability Pairing."
License Usage Considerations:
According to the documentation:
"You should use the IP address of the High Availability pair when requesting a High Availability license"
"If a license is only issued to the Active node in a High Availability pair, the system may not operate after failover to the Standby node"
"Both nodes must be up when requesting a license"
Why Other Options Are Incorrect:
A. If HA reboots, this is an indication of a problem - According to the documentation, reboots can
occur during the setup process: "Following the second reboot in the high availability setup, allow time for data synchronization" - this is normal, not an indication of a problem
B. Set up HA on the Secondary node first - Incorrect order. According to the documentation, "Before you begin setting up the Secondary node Forescout Platform device, verify that the Primary node Forescout Platform device is powered on" - the Primary node must be set up first
C. Connect devices to the network and to each other - While devices must be connected, this is a general infrastructure requirement, not specific to HA setup. The more specific requirement is licensing
D. HA needs to be manually configured on the secondary appliance in order to sync correctly - According to the documentation, the Secondary node configuration uses a setup process that is distinct from the Primary node: "When setting up the Secondary node device, use the same sync interfaces and netmask settings used in the Primary node device" - this is guided setup, not manual configuration for sync
High Availability Setup Process:
According to the documentation:
Set up Primary Node - "Select High Availability mode: 1) Standard Installation 2) High Availability C Primary Node"
Set up Secondary Node - "Set up a device as the secondary node" (secondary node connects to primary automatically)
Licensing - "You must install a permanent license before this period expires"
Referenced Documentation:
Forescout Resiliency Solutions User Guide (v8.0)
Forescout Installation Guide v8.1.x
Forescout Resiliency and Recovery Solutions User Guide v8.1
Set up and configure a device as the primary node
Set up a device as the secondary node
정답:
Explanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout DHCP Classifier Plugin Configuration Guide Version 2.1, the DHCP Classifier Plugin must be running for CounterACT to parse DHCP traffic. The documentation explicitly states:
"For endpoint DHCP classification, the DHCP Classifier Plugin must be running on a CounterACT device capable of receiving the DHCP client requests."
DHCP Classifier Plugin Function:
The DHCP Classifier Plugin is a component of the Forescout Core Extensions Module. According to the official documentation:
"The DHCP Classifier Plugin extracts host information from DHCP messages. Hosts communicate with DHCP servers to acquire and maintain their network addresses. CounterACT extracts host
information from DHCP message packets, and uses DHCP fingerprinting to determine the operating system and other host configuration information."
How the DHCP Classifier Plugin Works:
According to the configuration guide:
Plugin is Passive - "The plugin is passive, and does not intervene with the underlying DHCP exchange"
Inspects Client Requests - "It inspects the client request messages (DHCP fingerprint) to propagate DHCP information about the connected client to CounterACT"
Extracts Properties - Extracts properties like:
Operating system fingerprint
Device hostname
Vendor/device class information
Other host configuration data
DHCP Traffic Detection Methods:
The DHCP Classifier Plugin can detect DHCP traffic through multiple methods:
Direct Monitoring - The CounterACT device monitors DHCP broadcast messages from the same IP subnet
Mirrored Traffic - Receives mirrored traffic from DHCP directly
Replicated Messages - Receives DHCP requests forwarded/replicated from network devices
DHCP Relay Configuration - Receives explicitly relayed DHCP requests from DHCP relays
Plugin Requirements:
According to the documentation:
"No plugin configuration is required."
However, the plugin must be running on at least one CounterACT device for DHCP parsing to occur.
Why Other Options Are Incorrect:
A. Must see symmetrical traffic - While symmetrical network monitoring helps, it's not the requirement; the specific requirement is that the DHCP Classifier Plugin must be running
B. The enterprise manager must see DHCP traffic - Any CounterACT device capable of receiving
DHCP traffic can parse it, not just the Enterprise Manager
C. DNS client must be running - DNS services are not required for DHCP parsing; they are separate services
E. Plugin located in Network module - The DHCP Classifier Plugin is part of the Core Extensions Module, not the Network module
DHCP Classifier Plugin as Part of Core Extensions Module:
According to the documentation:
"DHCP Classifier Plugin: Extracts host information from DHCP messages."
The DHCP Classifier Plugin is installed with and part of the Forescout Core Extensions Module, which includes multiple components:
Advanced Tools Plugin
CEF Plugin
DHCP Classifier Plugin
DNS Client Plugin
Device Classification Engine
And others
Referenced Documentation:
Forescout DHCP Classifier Plugin Configuration Guide Version 2.1 About the DHCP Classifier Plugin documentation
Port Mirroring Information Based on Specific Protocols
Forescout Platform Base Modules
정답:
Explanation:
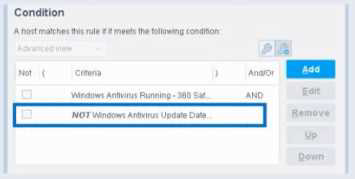
Based on the policy condition image provided showing the NOT checkbox on "Windows Antivirus Update Data", the correct statement is that the NOT operator negates the criteria inside the property.
Understanding the NOT Operator:
When the NOT checkbox is selected on a policy condition property, it performs a logical negation (NOT operation) on the criteria evaluation. According to the Forescout Administration Guide:
The NOT operator creates an inverted evaluation:
Without NOT: "Windows Antivirus Update Data = [value]"
Result: Matches endpoints where the property equals the specified value
With NOT (as shown in the image): "NOT (Windows Antivirus Update Data = [value])"
Result: Matches endpoints where the property does NOT equal the specified value
How the NOT Operator Works:
The NOT operator negates the criteria inside the property:
Criteria Evaluation - The property condition is evaluated normally first
Negation Applied - The result is then inverted (TRUE becomes FALSE, FALSE becomes TRUE) Final Result - The endpoint matches only if the negated condition is true Example from the Image:
The image shows:
First criterion: "Windows Antivirus Running - 360 Sat" (AND)
Second criterion: "NOT Windows Antivirus Update Data" (checked)
This means:
The endpoint must have Windows Antivirus Running = True (360 Sat)
AND the endpoint must NOT have the Windows Antivirus Update Data property value (whatever was specified)
The NOT negates the criteria inside the property condition
NOT vs. "Evaluate Irresolvable As":
According to the documentation, these are independent settings:
Setting Purpose
NOT Checkbox Negates the criteria evaluation (inverts the match logic)
Evaluate Irresolvable As Defines how to handle unresolvable properties (when data cannot be determined)
The NOT operator works inside the property evaluation, while "Evaluate Irresolvable As" is a separate setting that determines behavior when a property cannot be resolved.
Why Other Options Are Incorrect:
A. Irresolvable hosts would match the condition - The NOT operator doesn't specifically affect how irresolvable properties are handled
C. Negates the criteria outside the property - The NOT operator is internal to the property; it negates the criteria inside, not outside
D. Modifies the irresolvable condition to TRUE - The NOT operator doesn't modify the "Evaluate Irresolvable As" setting; these are independent
E. Negates the "evaluate irresolvable as" setting - The NOT operator and "Evaluate Irresolvable As" are separate; NOT doesn't affect or negate that setting
Policy Condition Structure:
According to the Forescout Administration Guide:
A policy condition is structured as:
text
[NOT] [Property Name] [Operator] [Value]
Where:
[NOT] - Optional negation operator (what the checkbox controls)
[Property Name] - The property being evaluated
[Operator] - The comparison operator (equals, contains, greater than, etc.)
[Value] - The value to match against
When NOT is checked, it negates the entire criteria evaluation inside that property condition.
Referenced Documentation:
Forescout Administration Guide v8.3
Forescout Administration Guide v8.4
Define policy scope documentation
Forescout eyeSight policy sub-rule advanced options
정답:
Explanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Switch Plugin Configuration Guide Version 8.12 and the Switch Properties documentation, the Switch IP/FQDN and Port Name property is used to identify an endpoint's connection location. The documentation explicitly states:
"The Switch IP/FQDN and Port Name property contains either the IP address or the fully qualified domain name of the switch and the port name (the physical connection point on that switch) to which the endpoint is connected."
Switch IP/FQDN and Port Name Property:
This property is fundamental for identifying where an endpoint is physically connected on the network. According to the documentation:
Purpose: Provides the exact physical location of an endpoint on the network by identifying:
Switch IP Address or FQDN - Which switch the endpoint is connected to Port Name - Which specific port on that switch the endpoint uses Example: A property value might look like:
정답:
Explanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout HPS Inspection Engine Configuration Guide Version 10.8 and the Remote Inspection and SecureConnector Feature Support documentation, the actions that can be performed with Remote Inspection include "Start Secure Connector" and "Attempt to open a browser at the endpoint".
Remote Inspection Capabilities:
According to the documentation, Remote Inspection uses WMI and other standard domain/host management protocols to query the endpoint, and to run scripts and implement remediation actions on the endpoint. Remote Inspection is agentless and does not install any applications on the endpoint.
Actions Supported by Remote Inspection:
According to the HPS Inspection Engine Configuration Guide:
The Remote Inspection Feature Support table lists numerous actions that are supported by Remote Inspection, including:
Set Registry Key - ✓ Supported by Remote Inspection
Start SecureConnector - ✓ Supported by Remote Inspection
Attempt to Open Browser - ✓ Supported by Remote Inspection
Send Balloon Notification - ✓ Supported (requires SecureConnector; can also be used with Remote Inspection)
Start Windows Updates - ✓ Supported by Remote Inspection
Send Email to User - ✓ Supported action
However, the question asks which actions appear together in one option, and Option D correctly combines two legitimate Remote Inspection actions: "Start Secure Connector" and "Attempt to open a browser at the endpoint".
Start SecureConnector Action:
According to the documentation:
"Start SecureConnector installs SecureConnector on the endpoint, enabling future management via SecureConnector"
This is a supported Remote Inspection action that can deploy SecureConnector to endpoints.
Attempt to Open Browser Action:
According to the HPS Inspection Engine guide:
"Opening a browser window" is a supported Remote Inspection action
However, there are limitations documented:
"Opening a browser window does not work on Windows Vista and Windows 7 if the HPS remote inspection is configured to work as a Scheduled Task"
"When redirected with this option checked, the browser does not open automatically and relies on the packet engine seeing this traffic"
Why Other Options Are Incorrect:
A. Set Registry Key, Disable dual homing - While Set Registry Key is supported, "Disable dual homing" is not a standard Remote Inspection action
B. Send Balloon Notification, Send email to user - Both are notification actions, but the question seeks Remote Inspection-specific endpoint actions; these are general notification actions not specific to Remote Inspection
C. Disable External Device, Start Windows Updates - While Start Windows Updates is supported by Remote Inspection, "Disable External Device" is not a Remote Inspection action; it's a network device action
E. Endpoint Address ACL, Assign to VLAN - These are Switch plugin actions, not Remote Inspection actions; they work on network device level, not endpoint level
Remote Inspection vs. SecureConnector vs. Switch Actions:
According to the documentation:
Remote Inspection Actions (on endpoints):
Set Registry Key on Windows
Start Windows Updates
Start Antivirus
Update Antivirus
Attempt to open browser at endpoint
Start SecureConnector (to deploy SecureConnector)
Switch Actions (on network devices):
Endpoint Address ACL
Access Port ACL
Assign to VLAN
Switch Block
Referenced Documentation:
Forescout CounterACT Endpoint Module HPS Inspection Engine Configuration Guide Version 10.8
Remote Inspection and SecureConnector C Feature Support documentation
Set Registry Key on Windows action documentation
Start Windows Updates action documentation
Send Balloon Notification documentation
정답:
Explanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Administration Guide and CounterACT Installation Guide, the important network traffic types that should be monitored by CounterACT include Web traffic, Authentication traffic, and DHCP.
Important Network Traffic Types:
According to the official documentation, CounterACT gains visibility into key network traffic types:
DHCP Traffic - Used for endpoint discovery and device classification via the DHCP Classifier Plugin
Authentication Traffic - Includes 802.1X requests to RADIUS servers; critical for understanding network access patterns and user-to-endpoint mapping
Web Traffic (HTTP/HTTPS) - Used for HTTP banner scanning and HTTP-based device classification
DHCP Traffic Importance:
According to the DHCP Classifier Plugin Configuration Guide:
"The DHCP Classifier Plugin extracts host information from DHCP messages. Hosts communicate with DHCP servers to acquire and maintain their network addresses. CounterACT extracts host information from DHCP message packets, and uses DHCP fingerprinting to determine the operating system and other host configuration information."
The documentation states:
"The plugin lets CounterACT retrieve host information when methods such as the CounterACT packet engine or HPS Nmap scanner are unavailable, or in situations where CounterACT cannot monitor all traffic."
Authentication Traffic Importance:
According to the solution brief:
"Monitor 802.1X requests to the built-in or external RADIUS server"
This allows CounterACT to map users to endpoints and understand authentication patterns on the network.
Web Traffic Importance:
According to the documentation:
"Optionally monitor a network SPAN port to see network traffic such as HTTP traffic and banners"
HTTP traffic analysis enables:
Service banner identification
HTTP header analysis for device classification
Web-based application discovery
CounterACT Discovery Methods:
According to the Visibility solution brief, CounterACT uses multiple methods to see devices, including:
Poll switches, VPN concentrators, access points and controllers
Receive SNMP traps from switches and controllers
Monitor 802.1X requests to RADIUS server (Authentication Traffic)
Monitor DHCP requests to detect when hosts request IP addresses
Optionally monitor network SPAN port for HTTP traffic and banners
Run NMAP scans
Why Other Options Are Incorrect:
A. Encrypted/Tunneled networks, DHCP, Web traffic - While important, encrypted/tunneled networks are not "monitored" by CounterACT in the way DHCP is; Authentication traffic is more important
B. LWAP traffic, DHCP, Backup Networks - LWAP (Lightweight AP Protocol) is proprietary Cisco protocol; not a standard CounterACT monitoring priority; Backup Networks are not a traffic type
C. Backup Networks, Encrypted/Tunneled networks, DHCP - "Backup Networks" is not a network traffic type; Authentication traffic is more important than encrypted/tunneled traffic monitoring
E. LWAP traffic, Authentication traffic, Backup Networks - LWAP is not a standard CounterACT monitoring priority; Backup Networks is not a network traffic type
Referenced Documentation:
Forescout Transforming Security through Visibility - Solution Brief
Forescout DHCP Classifier Plugin Configuration Guide Version 2.1
CounterACT Installation Guide - Network Access Requirements
정답:
Explanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
According to the Forescout Device Profile Library Configuration Guide, the Device Profile Library uses HTTP Banner (along with other properties like DHCP hostname, NIC vendor, and NMAP scan results) as key classification properties. When the Device Profile Library is updated, devices that were originally classified using HTTP Banner properties will be re-classified based on the new or updated profiles in the library.
Device Profile Library Function:
The Device Profile Library is a Content Module that delivers a library of pre-defined device classification profiles, each composed of properties and corresponding values that match a specific device type. According to the official documentation:
"Each profile maps to a combination of values for function, operating system, and/or vendor & model. For example, the profile defined for Apple iPad considers the set of properties which includes the hostname of the device revealed by DHCP traffic, the HTTP banner, the NIC vendor and Nmap scan results."
How Updates Impact Classification:
According to the documentation:
Library Updates - The Device Profile Library is periodically upgraded to improve classification accuracy and provide better coverage
Profile Changes - Updated profiles may change the properties used for classification or adjust matching criteria
Reclassification - When devices that rely on HTTP Banner information (or other matching properties in profiles) are re-evaluated against new profiles, their classification may change
Pending Changes - After a new version of the Device Profile Library is installed, devices show "pending classification changes" that can be reviewed before applying
Classification Properties in Device Profile Library:
According to the configuration guide, each device profile uses multiple properties including:
HTTP Banner - Information about web services running on the device (e.g., Apache 2.4, IIS 10.0)
DHCP Hostname - Device name revealed in DHCP traffic
NIC Vendor - MAC address vendor information
NMAP Scan Results - Open ports and services detected
When the Device Profile Library is updated, devices that were classified using these properties may be re-classified.
Why Other Options Are Incorrect:
A. Advanced Classification - This refers to custom classification properties, not DPL-based classification
B. External Devices - This is a classification category designation, not a classification method C. Client Certificates - This is used for certificate-based identification, not DPL classification E. Guest Registration - This is for guest management, not device classification via DPL Update Process:
According to the documentation:
"After a new version of the Device Profile Library is installed, it is recommended to run a policy that resolves classification properties. Due to classification profile changes in the new library version, some device classifications may change."
Before these changes are applied, administrators can review all pending changes and decide whether to apply them, modify existing policies first, or cancel the changes and roll back to a previous Device Profile Library version.
Referenced Documentation:
Forescout Device Profile Library Configuration Guide - February 2018 About the Device Profile Library documentation Update Classification Profiles section
정답:
Explanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
When troubleshooting an issue that affects multiple endpoints, you should view Policy logs before Host logs because Policy logs show details for a range of endpoints. According to the Forescout Administration Guide, Policy Logs are specifically designed to "investigate the activity of specific endpoints, and display information about how those endpoints are handled" across multiple devices.
Policy Logs vs. Host Logs - Purpose and Scope:
Policy Logs:
Scope - Shows policy activity across multiple endpoints simultaneously
Purpose - Investigates how multiple endpoints are handled by policies
Information - Displays which endpoints match which policies, what actions were taken, and policy evaluation results
Use Case - Best for understanding policy-wide impact and identifying patterns across multiple endpoints
Host Logs:
Scope - Shows detailed activity for a single specific endpoint
Purpose - Investigates specific activity of individual endpoints
Information - Displays all events and actions pertaining to that single host
Use Case - Best for deep-diving into a single endpoint's detailed history
Troubleshooting Methodology for Multiple Endpoints:
When troubleshooting an issue affecting multiple endpoints, the recommended approach is:
Start with Policy Logs - Determine which policy or policies are affecting the multiple endpoints
Identify Pattern - Look for common policy matches or actions across the affected endpoints
Pinpoint Root Cause - Determine if the issue is policy-related or host-related
Then Use Host Logs - After identifying the affected hosts, examine individual Host Logs for detailed troubleshooting
Policy Log Information:
Policy Logs typically display:
Endpoint IP and MAC address
Policy name and match criteria
Actions executed on the endpoint
Timestamp of policy evaluation
Status of actions taken
Efficient Troubleshooting Workflow:
According to the documentation:
When multiple endpoints are affected, examining Policy Logs first allows you to: Identify Common Factor - Quickly see if all affected endpoints are in the same policy Spot Misconfiguration - Determine if a policy condition is incorrectly matching endpoints Track Action Execution - See what policy actions were executed across the range of endpoints Save Time - Avoid reviewing individual host logs when a policy-level issue is evident Example Scenario:
If 50 endpoints suddenly lose network connectivity:
First, check Policy Logs - Determine if all 50 endpoints matched a policy that executed a blocking action
Identify the Policy - Look for a common policy match across all 50 hosts
Examine Root Cause - Policy logs will show if a Switch Block action or VLAN assignment action was
executed
Then, check individual Host Logs - If further detail is needed, examine specific host logs for those 50 endpoints
Why Other Options Are Incorrect:
A. Because you can gather more pertinent information about a single host - This describes Host Logs, not Policy Logs; wrong log type
C. You would not. Host logs are the best choice for a range of endpoints - Incorrect; Host logs are for single endpoints, not ranges
D. Policy logs may help to pinpoint the issue for a specific host - While true, this describes singular host troubleshooting, not multiple endpoints
E. Looking at Host logs is always the first step in the process - Incorrect; Policy logs are better for multiple endpoints to identify patterns
Policy Logs Access:
According to documentation:
"Use the Policy Log to investigate the activity of specific endpoints, and display information about how those endpoints are handled."
The Policy Log interface typically allows filtering and viewing multiple endpoints simultaneously, making it ideal for identifying patterns across a range of affected hosts.
Referenced Documentation:
Forescout Administration Guide - Policy Logs
Generating Forescout Platform Reports and Logs
Host Log C Investigate Endpoint Activity
"Quickly Access Forescout Platform Endpoints with Troubleshooting Issues" section in Administration Guide
정답:
Explanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
The Service Banner host property is resolved by NMAP scanning. According to the Forescout Administration Guide - Advanced Classification Properties, the Service Banner property "Indicates
the service and version information, as determined by Nmap".
Service Banner Property:
The Service Banner is an Advanced Classification Property that captures critical service identification information:
Purpose - Identifies running services and their versions on endpoints
Resolution Method - Uses NMAP banner scanning functionality
Information Provided - Service name and version numbers (e.g., "Apache 2.4.41", "OpenSSH 7.6")
NMAP Banner Scanning Configuration:
According to the HPS Inspection Engine Configuration Guide, the Service Banner is specifically resolved when "Use Nmap Banner Scan" option is selected:
When Use Nmap Banner Scan is enabled, the HPS Inspection Engine uses NMAP banner scans to improve the resolution of device services, application versions, and other details that help classify endpoints.
NMAP Banner Scan Process:
According to the CounterACT HPS Inspection Engine Guide, when NMAP banner scanning is enabled:
text
NMAP command line parameters for banner scan:
-T Insane -sV -p T: 21,22,23,53,80,135,88,1723,3389,5900
The -sV parameter specifically performs version detection, which resolves the Service Banner property by scanning open ports and identifying service banners returned by those services.
Classification Process:
The Service Banner property is resolved through the following workflow:
Port Detection - Forescout identifies open ports on the endpoint
Banner Scanning - NMAP sends requests to identified ports
Service Identification - Services respond with banner information containing version data
Property Resolution - The Service Banner property is populated with the version information discovered
Why Other Options Are Incorrect:
A. Packet engine - The Packet Engine provides network visibility through port mirroring, but does not resolve service banners through deep packet inspection
C. Device classification engine - While involved in overall classification, the Device Classification Engine doesn't specifically resolve service banners; NMAP does
D. Device profile library - The Device Profile Library contains pre-defined classification profiles but doesn't actively scan for service banners
E. NetFlow - NetFlow provides network flow data and statistics, but cannot determine service version information
Service Banner Examples:
Service Banner property values resolved by NMAP scanning include:
Apache/2.4.41 (Ubuntu)
OpenSSH 7.6p1
Microsoft-IIS/10.0
nginx/1.17.0
MySQL/5.7.26-0ubuntu0.18.04.1
NMAP Scanning Requirements:
According to the documentation:
NMAP Banner Scan must be explicitly enabled in HPS Inspection Engine configuration Banner scanning targets specific ports typically associated with common services Service version information improves endpoint classification accuracy Referenced Documentation:
Forescout Administration Guide - Advanced Classification Properties
HPS Inspection Engine - Configure Classification Utility
CounterACT Endpoint Module HPS Inspection Engine Configuration Guide Version 10.8
NMAP Scan Logs documentation
정답:
Explanation:
Comprehensive and Detailed Explanation From Exact Extract of Forescout Platform Administration and Deployment:
PXE (Preboot Execution Environment) boot endpoints should be exempt from Assessment policies because they are not yet manageable and may not have all the required software and services installed. According to the Forescout Administration Guide, endpoints in the early stages of deployment, such as those booting via PXE, are temporary in nature and lack the necessary management capabilities and required software components.
PXE Boot Endpoints Characteristics:
PXE boot endpoints represent machines in a temporary state during the deployment process:
Not Yet Fully Deployed - PXE boot is used during initial OS installation and deployment
Lack Required Services - The endpoint does not yet have installed:
SecureConnector (if required for management)
Endpoint agents
Required security software
Management services
Limited Configuration - The endpoint may not have completed network configuration
Temporary State - PXE boot endpoints are in a transient state, not their final operational state
Policy Endpoint Exceptions:
According to the documentation, administrators can "select endpoints in the Detections pane and exempt them from further inspection for the policy that detected them". This is particularly important for PXE boot endpoints because:
False Positives - Assessment policies might flag PXE boot endpoints as non-compliant due to missing software that hasn't been installed yet
Blocked Deployment - If blocking actions are applied, they could interfere with the deployment process
Temporary Assessment - Once the endpoint is fully deployed and manageable, it can be added back to Assessment policies
Operational Efficiency - Exempting PXE boot endpoints prevents unnecessary policy violations during the deployment window
Manageable vs. Unmanageable Endpoints:
According to the documentation:
"Endpoints are generally unmanageable if their remote registry and file system cannot be accessed by Forescout. Unmanageable hosts can be included in your policy."
PXE boot endpoints specifically fall into this category because:
Remote management is not yet available
Required agents are not installed
File system access is not established
Why Other Options Are Incorrect:
A. Because they will not be subject to the Acceptable Use Policy - Not the primary reason; Assessment policies differ from Acceptable Use policies
B. They have already been deployed and should immediately be subject to Assessment policies - Contradicts the purpose; PXE boot endpoints are NOT yet deployed
D. Because they will never be manageable or have the required software and services - Incorrect; once deployed, they WILL become manageable
E. Because they are special endpoints playing a specific role in the network - While true in context, this doesn't explain why they need exemption
Referenced Documentation:
Forescout Administration Guide - Create Policy Endpoint Exceptions Restricting Endpoint Inspection documentation Manage Actions - Unmanageable hosts section