Dell PowerProtect Cyber Recovery Deploy v2 Exam 온라인 연습
최종 업데이트 시간: 2025년11월23일
당신은 온라인 연습 문제를 통해 DELL EMC D-PCR-DY-01 시험지식에 대해 자신이 어떻게 알고 있는지 파악한 후 시험 참가 신청 여부를 결정할 수 있다.
시험을 100% 합격하고 시험 준비 시간을 35% 절약하기를 바라며 D-PCR-DY-01 덤프 (최신 실제 시험 문제)를 사용 선택하여 현재 최신 38개의 시험 문제와 답을 포함하십시오.
정답: 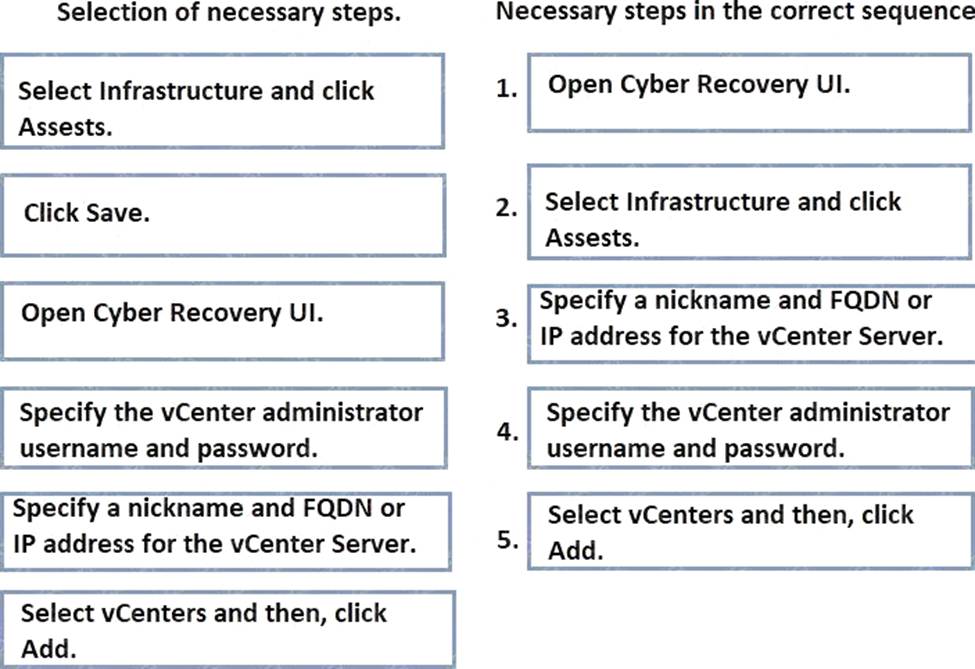
정답:
Explanation:
The command crsetup.sh --install is used to configure the Dell PowerProtect Cyber Recovery software on the management host, setting up necessary components and services.
정답:
Explanation:
Data must be stored in a PowerProtect Data Domain MTree within the production environment and then replicated to the vault environment to ensure data protection and isolation for recovery.
정답:
Explanation:
Alert 2035 notifies the administrator of communication errors with a Data Domain system.
The Cyber Recovery GUI reflects this by changing the vault status to "Unknown," indicating loss of connection.
정답:
Explanation:
The CyberSense Alerts dashboard includes alerts for threshold exceeded conditions, indicating when certain monitored metrics surpass predefined limits, and timed out alerts, indicating when processes or scans do not complete within expected timeframes.
정답:
Explanation:
A Denial of Service (DoS) attack overwhelms system resources by flooding it with excessive requests, exhausting capacity and causing service disruption.
정답:
Explanation:
vCenter hosting PowerProtect Data Manager must be added to Dell PowerProtect Cyber Recovery to enable automated recovery processes. This integration allows Cyber Recovery to manage and automate the recovery workflows directly through the virtual infrastructure.
정답:
Explanation:
The minimum configuration to deploy the Dell PowerProtect Cyber Recovery OVA on VMware ESXi includes vCenter or ESXi version 7.0 or 8.0, with 3 disks, 4 CPUs, and 8 GB of memory to meet performance and storage requirements.
정답:
Explanation:
Using Dell PowerProtect Data Domain in an isolated clean room serves as a secure target for alternate recovery, providing a protected environment to restore data if the primary vault is compromised.
정답:
Explanation:
Deploying the CyberSense virtual appliance with a large configuration requires 32 vCPU and 384 GB of RAM to handle the processing and memory demands efficiently.
정답:
Explanation:
Dell Technologies recommends performing an initial replication between the production and vault systems for each replication context before defining Cyber Recovery policies to ensure data consistency and establish a baseline for ongoing replication and protection.
정답:
Explanation:
To ensure the report includes the latest data, the IT manager should generate a new report using the Report Wizard, which reruns the report query and produces an updated output