Associate VMware Security 온라인 연습
최종 업데이트 시간: 2025년11월17일
당신은 온라인 연습 문제를 통해 VMware 1V0-81.20 시험지식에 대해 자신이 어떻게 알고 있는지 파악한 후 시험 참가 신청 여부를 결정할 수 있다.
시험을 100% 합격하고 시험 준비 시간을 35% 절약하기를 바라며 1V0-81.20 덤프 (최신 실제 시험 문제)를 사용 선택하여 현재 최신 55개의 시험 문제와 답을 포함하십시오.
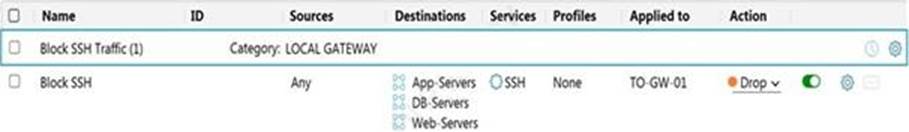
정답:
정답:
Explanation:
Reference: https://docs.vmware.com/en/VMware-NSX-T-Data-Center/3.1/administration/GUID-8F3CB282-B38E-49E1-951A-7D6B972B1FB7.html
정답:
Explanation:
Reference: https://blogs.vmware.com/vsphere/2020/02/good-security-thrives-in-simplicity.html
정답:
정답:
Explanation:
Reference: https://www.vmware.com/content/dam/digitalmarketing/vmware/en/pdf/products/nsx/vmware-nsx-datasheet.pdf
정답:
정답:
Explanation:
Reference: https://docs.vmware.com/en/VMware-Workspace-ONE-Access/20.01/ws1_access_authentication/GUID-3D7AB065-E2ED-4525-B575-2A576BAA3CC3.html
정답:
Explanation:
Reference: https://docs.vmware.com/en/VMware-Workspace-ONE-UEM/services/Windows_Desktop_Device_Management/GUID-uemWindeskProfiles.html
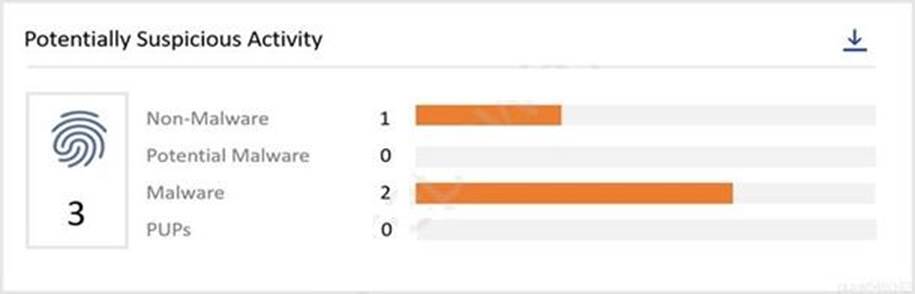
정답:
Explanation:
Reference: https://docs.vmware.com/en/VMware-Carbon-Black-Cloud/services/carbon-black-cloud-user-guide.pdf (15)
정답:
정답:
Explanation:
Reference: https://docs.vmware.com/en/VMware-Workspace-ONE/services/intelligence-documentation/GUID-21_intel_automations.html
정답:
Explanation:
Reference: https://www.kaspersky.com/resource-center/definitions/what-is-jailbreaking
정답:
Explanation:
Reference: https://docs.vmware.com/en/VMware-Workspace-ONE/services/intelligence-documentation/GUID-01_intel_intro.html#:~:text=Access%20Workspace%20ONE%20Intelligence&text=Access %20the%20reports%20by%20navigating,console%2C%20follow%20the%20required%20st eps
정답:
Explanation:
Reference: https://www.vmware.com/content/dam/digitalmarketing/vmware/en/pdf/docs/vmwcb-enterprise-edr-datasheet.pdf (2)
정답: